Runtime-based vulnerability management
Prioritize Critical Vulnerabilities with Runtime Context and Threat Intelligence, Reducing CVE-Related Work by 90%+
Using a unique eBPF runtime sensor, ARMO Platform creates workloads’ SBOM and analyzes which libraries and components are “in-use”, meaning loaded into memory and executed in runtime.
Focus on real risks, not on {CVEs}
Gain Insightful Prioritization
ARMO Platform enables precise vulnerability prioritization by analyzing container image SBOMs, together with workload context, exploitability (EPSS and KEV), severity (CVSS), runtime analysis (CVEs “in-use”), and fixability.
This comprehensive approach ensures that you address the most critical vulnerabilities first, minimizing potential risks to your infrastructure.
Real-Time Threat Intelligence Integration
Stay ahead of emerging threats with real-time insights gathered from multiple threat intelligence sources, including CISA-KEV (Known Exploitable Vulnerabilities) and EPSS (Exploit Prediction Scoring System), as well as the CVSS (Common Vulnerability Scoring System).
Combining this data with specific runtime-based vulnerable components lets you quickly spot exploitable vulnerabilities and take proactive steps to address them.
360° view of your Kubernetes-related vulnerabilities
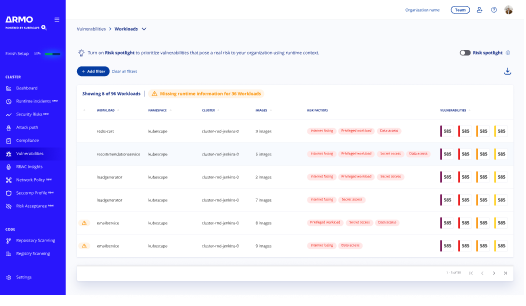
/ ARMO Platform offers different views of your vulnerabilities
Workloads view – see all workloads across all your environments. sort and filter workloads by various risk factors, such as external facing, privileged, data access, secrets access, host access, and more.
CVEs view – see all the CVEs across all your environments. Search for a specific CVE, or sort and filter CVEs by various criteria, such as severity, exploitability, patch availability, and more.
Images view – see all the images across all your environments and their vulnerabilities. You will also be able to see the CVEs in each image layer such as the application layer and the base layer.
Components view – see all the components across all your environments and the CVEs that affect each component, which of them are ‘In Use’, and the impact that they have on your assets.
Reduce CVE-related toil by 90%
Save time and resources by prioritizing reachable and exploitable vulnerabilities using runtime context and advanced threat intelligence information.
Risk spotlight
With one click, identify vulnerabilities that require immediate attention
Apply real-time threat intelligence
Real-time threat intelligence from multiple sources, such as CISA-KEV and EPSS, allows you to stay ahead of emerging threats and quickly identify actively exploitable vulnerabilities.
Leverage 360° view of risk
Utilize different views of your vulnerabilities, to see all workloads, CVEs, images, and components across all your environments, sort and filter them to gain a comprehensive understanding of your vulnerabilities.



