Continuous Cloud Security Posture Management (CSPM)
Get full visibility into your critical cloud assets and audit them against the most comprehensive security and compliance frameworks with ARMO's agentless scanning
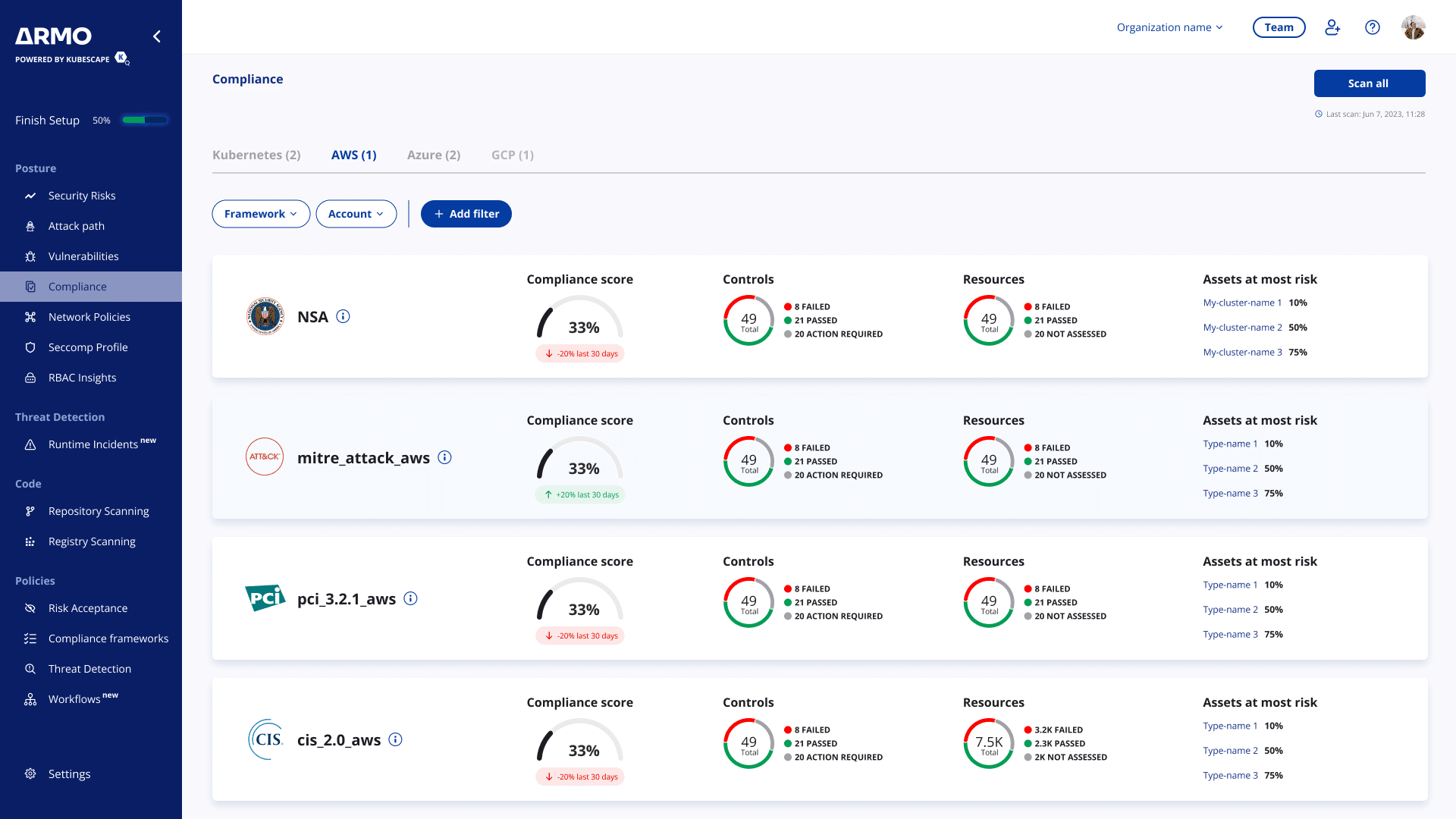
Choose the compliance framework that you need
For the cloud environment you use
Agentless Scanning
Configurations and vulnerability scanning plus Cloud Detection & Response (CDR) - all using agentless scanning.
Total Cloud Visibility
Get complete visibility into your critical cloud assets, analyze cloud events and keep track of compliance drifts in real time.
Multi-Cloud Support
Analyzes AWS, GCP, Azure, and more environments for security misconfigurations and compliance gaps.
Cloud Security Risks
Analyze your cloud security posture according to broad risk categories and specific severity-based controls.
Actionable Compliance Remediations
Fix failing controls and achieve compliance with detailed remediation steps.
Unified View and Detailed Reporting
A centralized dashboard that displays compliance information across multiple clouds, including passing scores, failing requirements, and resource violations according to severity.
/ See ARMO Platform’s CSPM in action
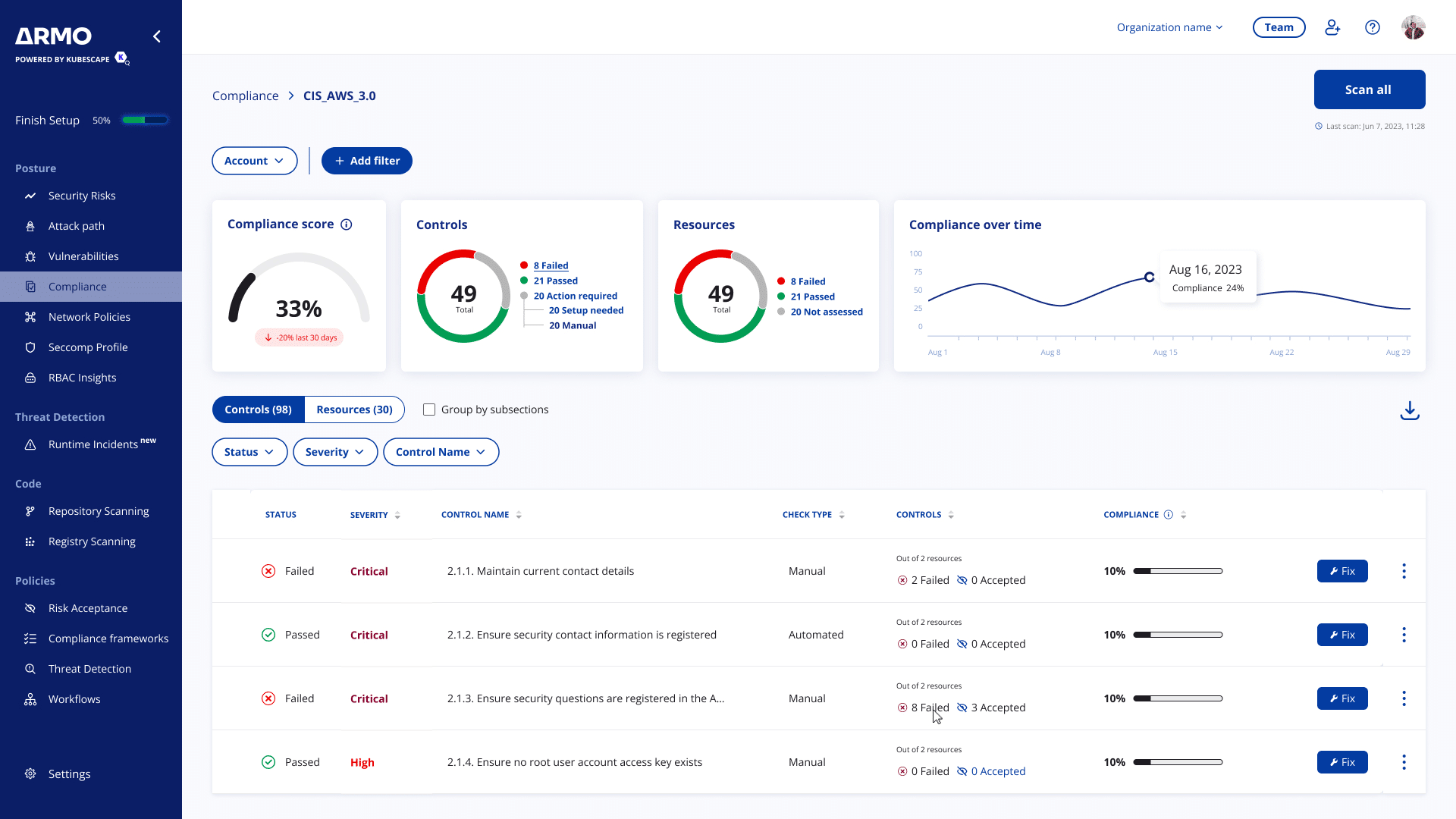
ARMO Cloud Risk Categories and Controls
ARMO Platform offers a comprehensive set of controls spanning the most critical risk categories relevant to cloud infrastructure and application security. Each control will be rated as passed or failed, along with the recommended remediation steps
Data Security
- Misconfigured S3 Bucket
- Unencrypted Data at Rest
- Publicly Accessible Databases
- Insecure API Gateway
- Insecure Cloud Storage Access
Identity Security
- Weak IAM Policies
- Lack of Multi-Factor Authentication
- Misconfigured Identity Providers
- Excessive Privileges
Network Security
- Misconfigured Security Groups
- Lack of Network Segmentation
- Insufficient DDoS Protection
Application Security
- Insecure API Gateway
- Outdated SSL/TLS Certificates
Vulnerability Management
- Unpatched Cloud Instances
Monitoring & Logging
- Insufficient Logging and Monitoring
Data Protection
- Inadequate Backup and Recovery
Cryptography
- Poor Key Management Practices
Your Cloud Security, Simplified
Get expert advice tailored to your needs

Ben Hirschberg
CTO & Co-Founder

Oshrat Nir
Head of Product Marketing

Amit Schendel
Security researcher





