Secure your containers from code to cloud
Loved by DevOps and trusted by Security at_
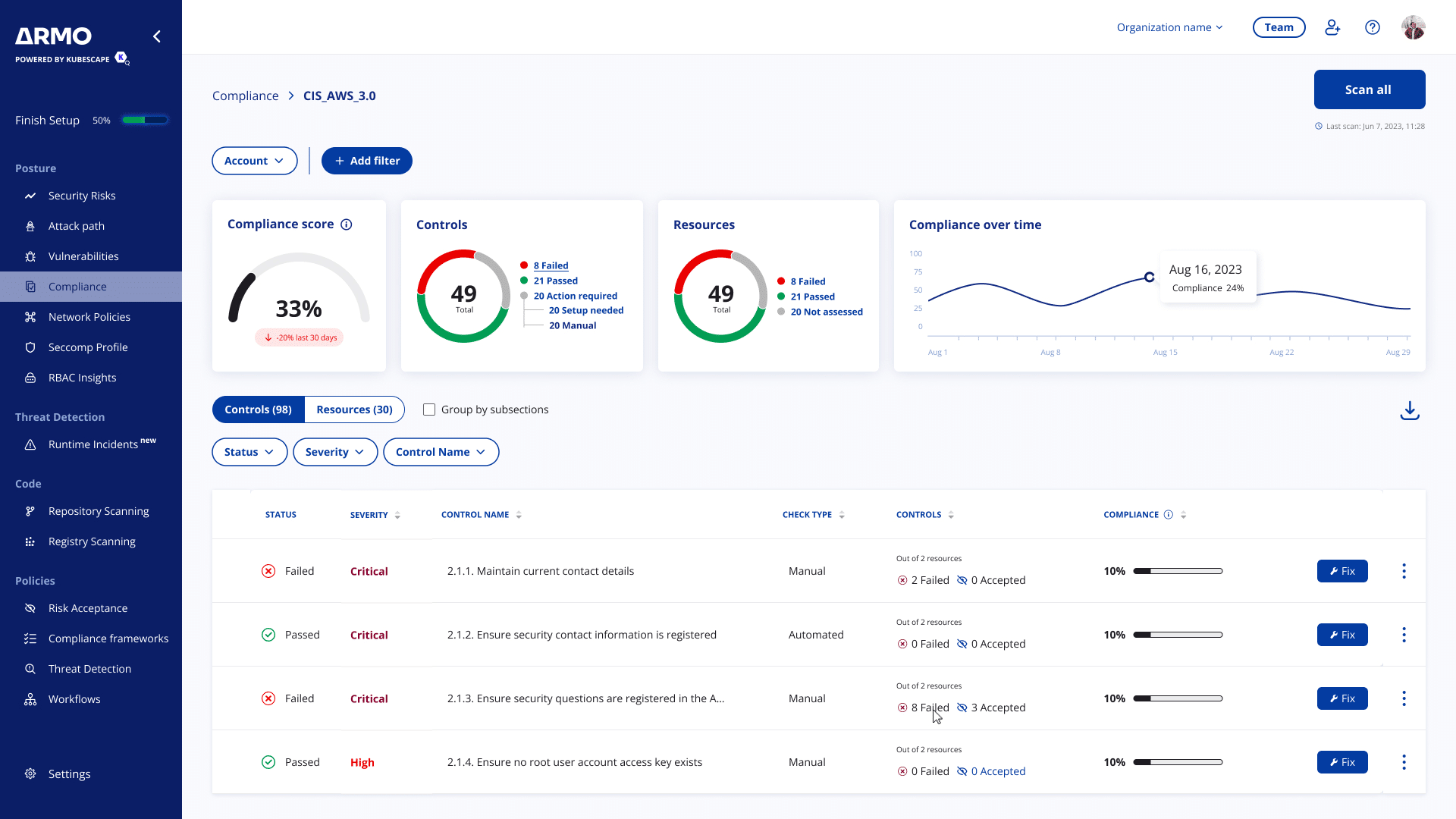
Complete Visibility
Discover and scan all your containers, hosts, clusters, and cloud assets to build a complete view of your containerized environments.
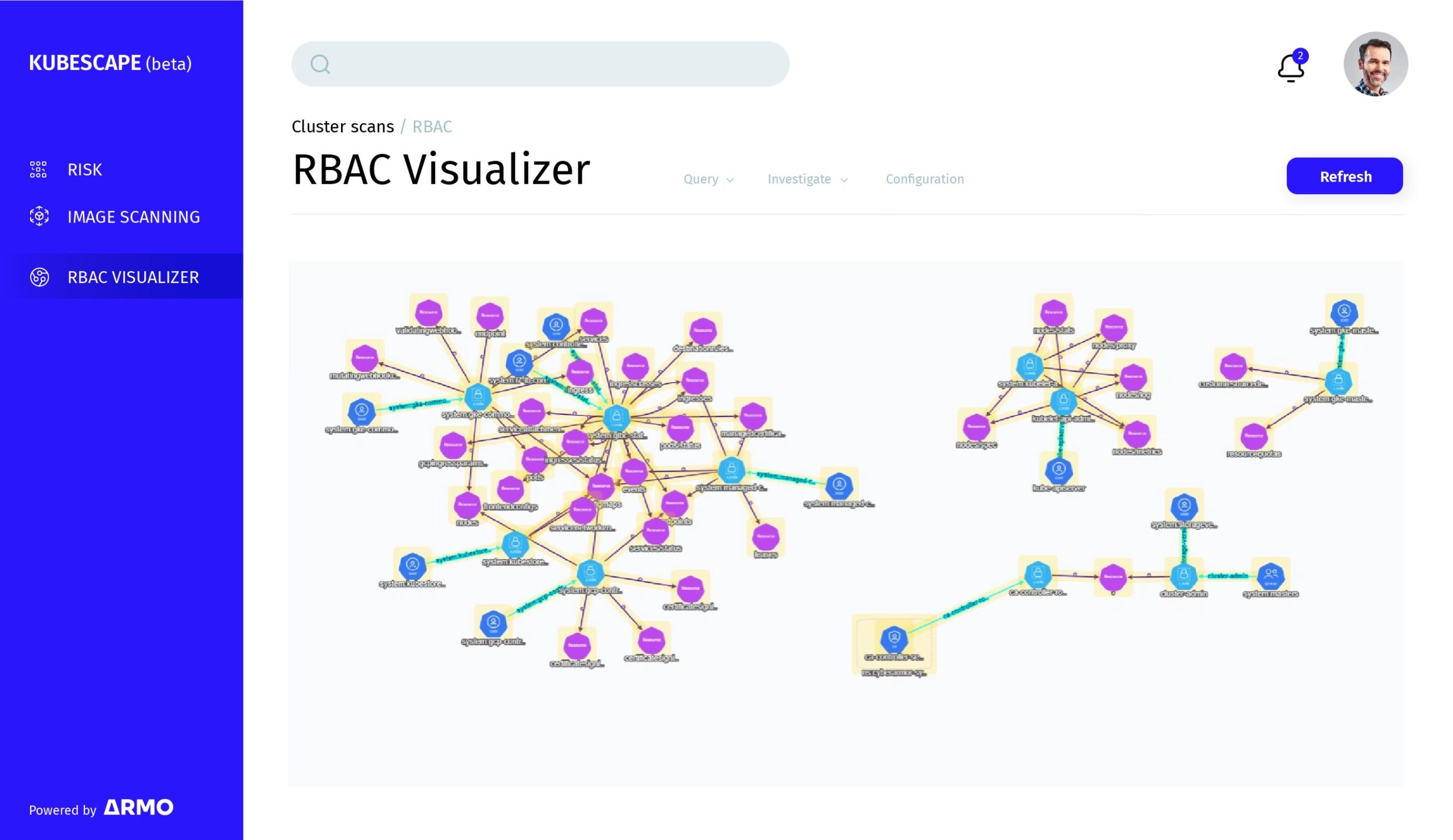
Shift Left
Secure container images from IDE into run-time and ensure security compliance while deploying.
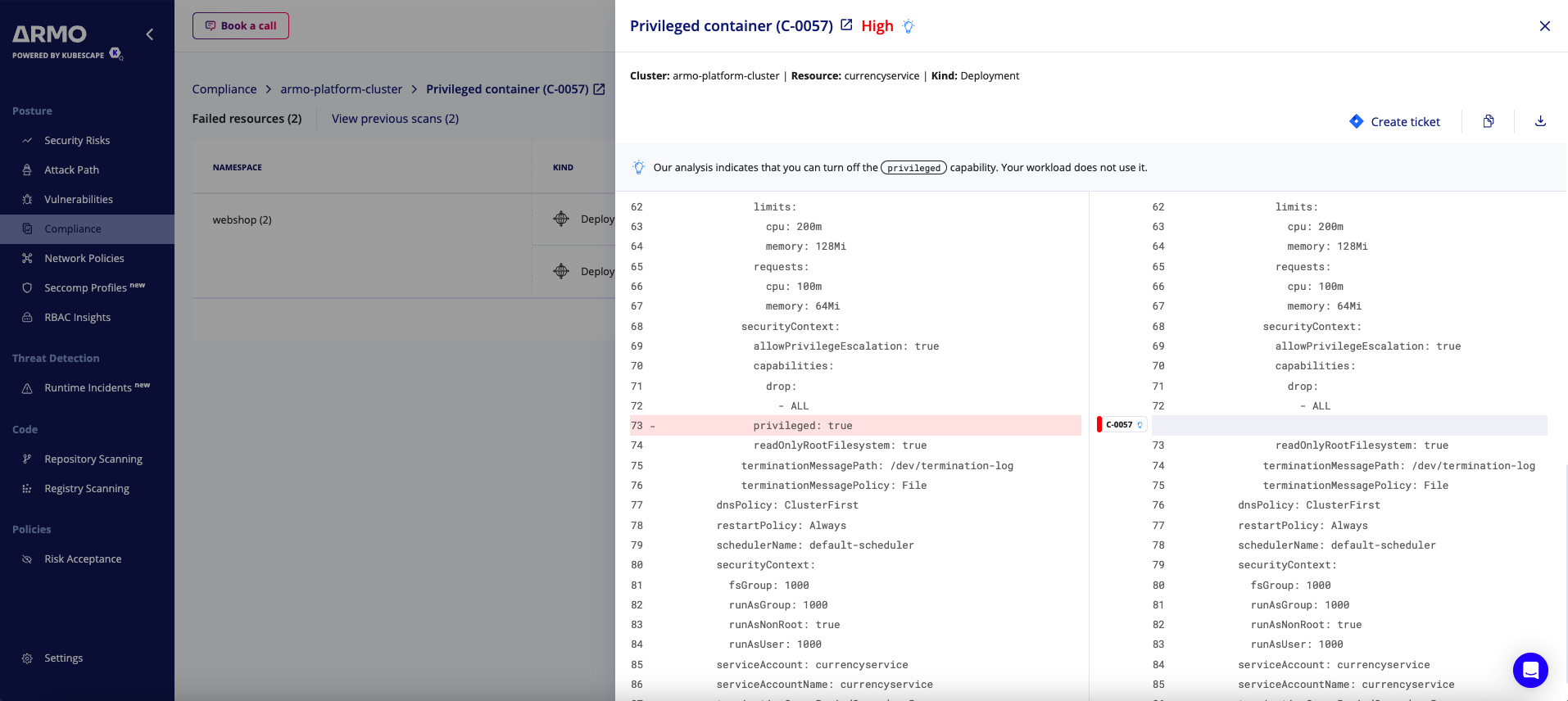
Smart Remediation
Remediate security risks without interfering with application uptime. ARMO Platform’s eBPF runtime sensor analyzes application behavior to ensure that recommended fixes are both safe and effective.
Eliminate Guesswork
Discover, prioritize, and automatically remediate the most critical security issues based on runtime exposure and real risks, without interfering with application uptime.
Runtime-based Vulnerability Management
Redcue CVE-related work by 90% – prioritize critical container images vulnerabilities with runtime context and threat intelligence.

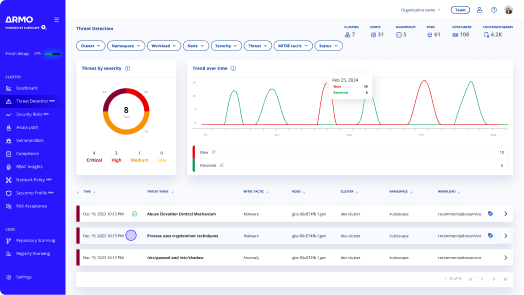
Threat Detection & Response
Protect your containerized applications and workloads from cyberattacks before they happen and quickly respond to them, without being overwhelmed by alerts using anomaly detection powered by eBPF.
The value our users see in ARMO Platform



{Flexible hosting options}
Hosted by ARMO
We’ll host your ARMO Platform instance and retain your data (SOC 2 compliant), according to the plan you are on.
In your cloud
Install ARMO Platform as a private tenant on your cloud provider account and host your data yourself.
On-Prem
Install ARMO Platform on your on-prem machines
