Get Efficient with Automatic Kubernetes Compliance
Loved by DevOps and trusted by Security at_

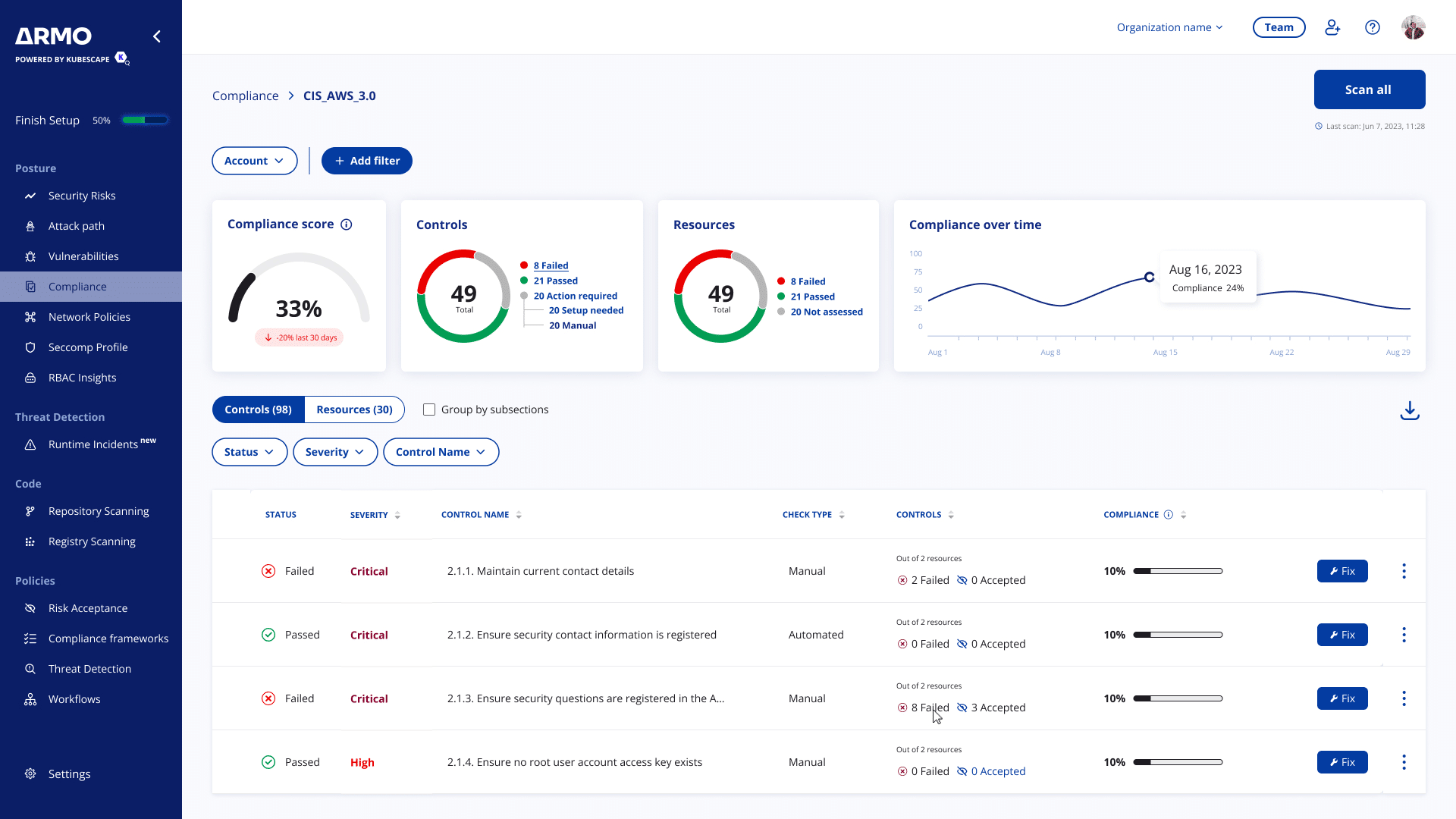
Automatic Kubernetes Compliance
Over 90% of the necessary compliance checks are automated, making it easy to meet compliance requirements (CIS, NSA, Mitre, SOC2, PCI, and more), without overwhelming your DevOps and security teams.
K8s compliance made easy
Get through your Kubernetes compliance audit with flying colors by using accepted frameworks. ARMO Platform is an auditor approved product that easily illuminates Kubernetes security vulnerabilities tagged by priority.
Smart Remediation
Remediate security risks without interfering with application uptime. ARMO Platform’s eBPF runtime sensor analyzes application behavior to ensure that recommended fixes are both safe and effective. The platform provides a side-by-side view comparing proposed changes with existing code. This comparison is enhanced by runtime context, which helps guarantee that any modifications will not disrupt the application’s normal functionality during execution.
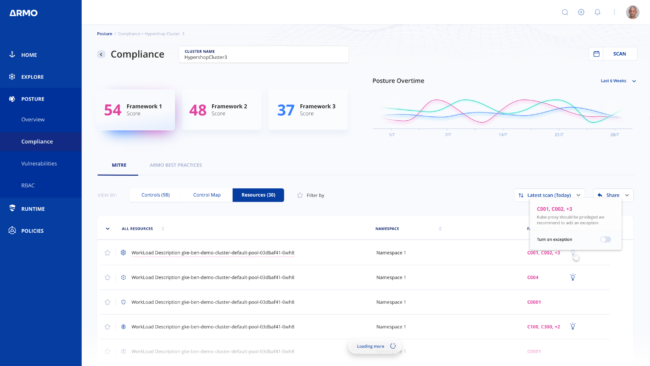
Frameworks galore
Scan your clusters against industry standards such as NSA-CISA, CIS, and MITRE ATT&CK -OR- Create your own frameworks – meet your unique security needs and audit requirements by building a custom framework from available controls.
The value our users see in ARMO Platform








{Flexible hosting options}
Hosted by ARMO
We’ll host your ARMO Platform instance and retain your data (SOC 2 compliant), according to the plan you are on.
In your cloud
Install ARMO Platform as a private tenant on your cloud provider account and host your data yourself.
On-Prem
Install ARMO Platform on your on-prem machines

 Continue as a guest
Continue as a guest