AWS Security Best Practices
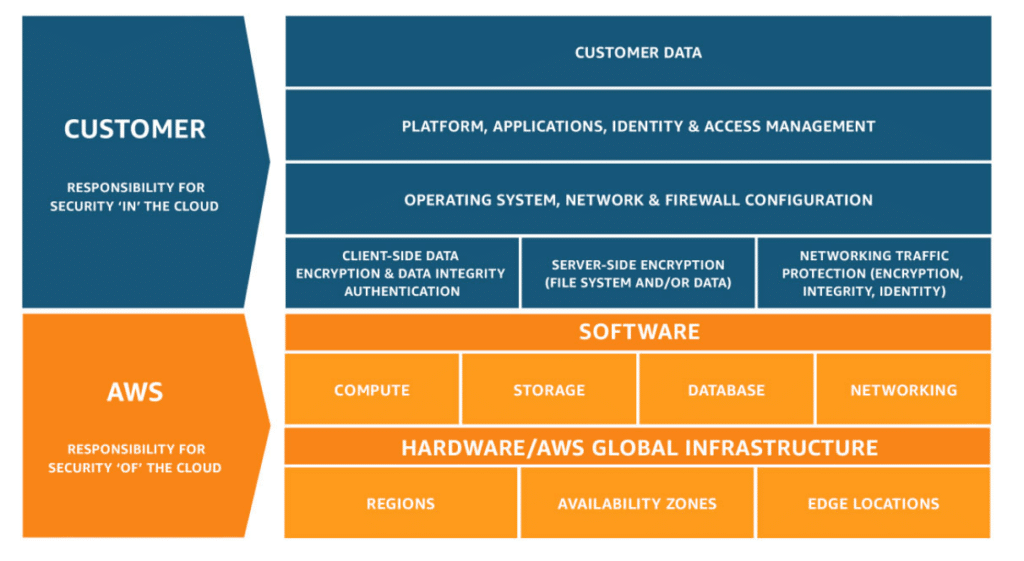
Amazon Web Services (AWS) operates under a shared responsibility model for cloud security. AWS secures the cloud infrastructure, while customers are responsible for protecting their applications, data, and configurations within the cloud environment.
Following AWS security best practices is essential to mitigate risks, meet compliance requirements, and ensure data protection across cloud services. These practices involve multiple layers of security, including identity and access management, network security, data protection, incident response, disaster recovery, and specialized security strategies for Kubernetes deployments and Infrastructure as Code (IaC).
Shared Responsibility Model
Under the shared responsibility model, AWS and its customers each have specific security responsibilities. While AWS is responsible for securing the infrastructure—such as physical data centers, networks, and virtualization environments—customers need to secure their resources within the AWS ecosystem. This includes protecting their data, managing user access, configuring network settings, and ensuring the security of their applications and workloads.
Key Principles of AWS Security
To build a robust security posture in the cloud, follow these key principles:
1. Least privilege access
Apply the principle of least privilege by giving users, applications, and services only the permissions they need to perform their tasks. This minimizes the attack surface in your AWS environment, reducing the risk of unauthorized access and security breaches. Regularly audit and update permissions to ensure they are aligned with current roles and responsibilities, preventing excess access and protecting critical resources.
2. Zero trust architecture
Adopt a zero-trust approach, assuming that breaches have already occurred. Verify every user, device, and application before granting access to reduce the attack surface and enhance overall security.
3. Defense in depth
Implement multiple layers of security controls, such as access management, cloud network security, and data encryption, to create a comprehensive defense against threats.
4. Security by design
Integrate security considerations into the architecture and design of cloud applications from the outset to prevent vulnerabilities and streamline compliance.
Identity and Access Management (IAM)
One of the core elements of AWS security is effective identity and access management (IAM). AWS offers several tools and best practices to enforce secure access:
- Use IAM policies and roles to control access based on the principle of least privilege. Define specific roles and policies for users and services to ensure appropriate access levels.
- Enable multi-factor authentication (MFA) for all users, particularly those with elevated privileges, to mitigate credential theft risks.
- Treat access keys like passwords and regularly rotate them for IAM users to minimize the exposure of sensitive credentials.
- Centralize management with AWS Organizations and Service Control Policies (SCPs) to manage multiple AWS accounts from a single point and apply security guardrails.
Network Security in AWS
Securing your network infrastructure is crucial to prevent unauthorized access and minimize the attack surface. Here’s how to keep it secure.
Configure VPCs thoughtfully
Use Virtual Private Clouds (VPCs) to create isolated network environments. Restrict public subnets to resources that need public access, such as web servers, and keep sensitive data in private subnets.
Implement security groups and NACLs
Utilize security groups and network access control lists (NACLs) as cloud-based firewalls to control inbound and outbound traffic. Make rules tight and specific to reduce the attack surface.
Use AWS WAF for web protection
Deploy AWS Web Application Firewall (WAF) to protect applications from common web exploits like SQL injection and cross-site scripting (XSS).
Data Protection and Encryption
Protecting your data, both at rest and in transit, is essential for maintaining the confidentiality and integrity of your information. Follow these data protection and encryption best practices:
1. Enable encryption everywhere
Use AWS Key Management Service (KMS) to encrypt data at rest and always use SSL/TLS for data in transit. This prevents unauthorized access, whether data is stored or moving between locations.
2. Monitor encryption policies
Regularly audit your environment to ensure compliance with your organization’s encryption policies.
3. Manage data lifecycle wisely
Implement secure data lifecycle management practices, such as using S3 Lifecycle policies to automatically transition data between different storage classes or delete it when no longer needed.
Logging, Monitoring, and Incident Response
Effective logging, monitoring, and incident response capabilities are essential for detecting, investigating, and responding to security incidents. To enhance AWS security, enable AWS CloudTrail to capture and monitor all API activity for auditing and forensics, ensuring a comprehensive log of actions taken across your environment.
Configure Amazon GuardDuty to automatically detect suspicious activities and potential threats, providing continuous monitoring and threat detection to safeguard your resources. Set up Amazon CloudWatch to monitor anomalies in metrics and logs and generate alerts for any potential security issues, enabling rapid response to incidents.
Finally, establish a centralized log management strategy that efficiently collects, stores, and analyzes logs from various AWS services. This will make it easier to correlate events and identify security threats across your cloud environment.
Infrastructure Security and Compliance
Maintaining the security and compliance of your AWS infrastructure is an ongoing process:
- Regularly apply patches and updates to all software and systems to mitigate known vulnerabilities.
- Conduct regular security audits and penetration testing to identify and address security gaps in your AWS resources and applications.
- Leverage AWS Security Hub to aggregate, organize, and prioritize security alerts from multiple AWS services and third-party security tools.
- Implement compliance as code using tools like AWS Config and AWS CloudFormation Guard to automate compliance checks and enforcement.
Kubernetes-Specific Security Practices on AWS
For organizations running Kubernetes on AWS, consider the following security best practices:
- Run Kubernetes nodes in private subnets to restrict direct access and minimize the attack surface.
- Use Amazon Elastic Kubernetes Service (EKS) to leverage AWS-managed Kubernetes infrastructure, reducing the operational overhead.
- Implement Pod Security Standards (PSS) to enforce least privilege policies for your Kubernetes pods and containers.
- Integrate AWS Identity and Access Management with Kubernetes using IAM Roles for Service Accounts (IRSA) to manage permissions more effectively at the pod level.
Automated Security and Infrastructure as Code
To enhance the security and reliability of your AWS environment, use IaC tools like Terraform and AWS CloudFormation to automate security configurations. This approach ensures consistent deployment and minimizes the risk of human error, maintaining a stable and secure infrastructure.
Integrating security into CI/CD pipelines is also critical. By embedding security checks into the deployment process, you can identify and fix security vulnerabilities before they reach production, protecting applications and data from potential threats.
Additionally, compliance can be continuously monitored by leveraging tools like AWS Config. These tools allow you to track your compliance status and automatically correct any deviations, ensuring the cloud environment remains secure and aligned with regulatory requirements.
Incident Response and Disaster Recovery
When it comes to incident response and disaster recovery, preparation is essential to minimize damage and ensure quick recovery.
Start by creating comprehensive incident response plans that are regularly updated and tailored to your AWS environment. These plans should incorporate elements such as IAM policies, GuardDuty findings, and CloudTrail logs. This will ensure that your team knows exactly what to do in the event of a security incident.
Automate backups and snapshots to secure your data; these measures help maintain data integrity and availability by enabling swift restoration if an incident occurs. It’s also crucial to regularly test and validate disaster recovery strategies. Identifying gaps and making necessary improvements enhances the organization’s readiness to respond effectively to any disruption.
Proactive Cloud Security
As cloud security threats evolve, so too must your strategies and practices—be vigilant, adapt quickly, and always prioritize security as an ongoing, integral part of your cloud operations.
Adopt a holistic approach that combines technical controls, automation, and proactive monitoring. Leveraging AWS-native tools and cloud-agnostic solutions such as Cloud Security Posture Management (CSPM) helps ensure comprehensive protection across the cloud environment. Additionally, you need to stay current with the latest trends and AWS cloud security updates.




