Best ADR Security Solutions in 2026: Why Full-Stack Visibility Beats Siloed Alerts
Key Insights What is ADR (Application Detection & Response)? A security tool that monitors application-layer...

Jun 26, 2022
With Kubernetes adoption continuing to rise, we’ve seen multiple studies add to the growing body of research for enterprise K8s deployments this past year. Companies leveraging managed services and packaged platforms drive much of the continued growth in adoption. An annual study conducted by the Cloud Native Computing Foundation (CNCF) found that 96% of organizations surveyed are either using or evaluating K8s currently. 5.6 million developers use K8s worldwide, accounting for 31% of all backend developers across the globe.
Survey respondents using K8s cite improved scalability and availability and shorter deployment times as the main reason for leveraging the technology. Among those users, weekly and daily release cadences are commonplace. While the number of organizations leveraging K8s will only continue to grow, there are rising concerns about security.
According to Gartner, through 2025, more than 99% of cloud breaches will have a root cause of customer misconfigurations or mistakes. This matches up with the findings from Gartner’s 2021 Hype Cycle for Cloud Security report which shows that 59% of security incidents with known causes occurred from a detected misconfiguration. When asked which risks concerned cloud leaders the most for their containers and K8s environments, most respondents identified misconfigurations as their number 1 concern.
K8s users and organizations fight misconfiguration and vulnerabilities across the SDLC. Kubescape is a Kubernetes open-source security platform providing a multi-cloud K8s single pane of glass, including risk analysis, security compliance, RBAC visualizer, and image vulnerability scanning.
Kubescape scans K8s clusters, YAML files, HELM charts, worker nodes and APIs servers, detecting misconfigurations according to multiple frameworks (such as the NSA-CISA, MITRE ATT&CK, and more), software vulnerabilities, and RBAC (role-based-access-control) violations across the SDLC, calculates risk score instantly and shows risk trends over time.
Since we launched Kubescape in August 2021, it has scanned more than 10,000 K8s clusters. We aggregated the data and did some analysis to highlight essential stats on the state of K8s security, risk, and compliance.
Here are the main conclusions:
Our scans included implementations across multiple regions, including North America, Europe, the Middle East, Africa, and the Asia Pacific. Our users range from DevOps and DevSecOps engineers to security engineers, architects, and risk analysts.
So what have we learned?
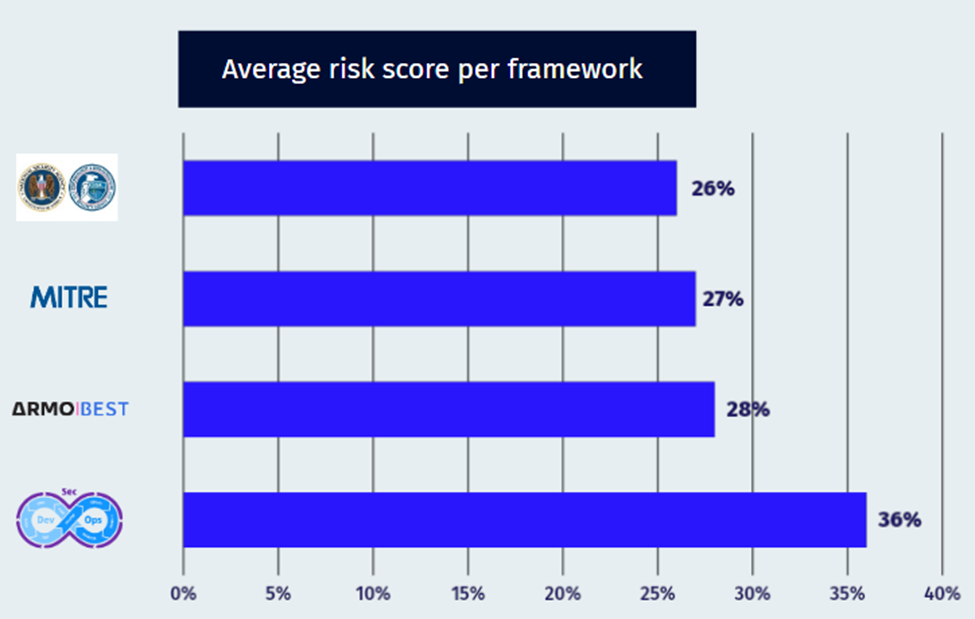
We assessed our findings in four frameworks, including ArmoBest, MITRE ATT&CK, NSA-CISA Hardening guidance, and DevOps Best Practices.
For each assessment, 100 represents the highest risk and 0 the lowest. A best practice is for organizations to keep their risk scores below 30, with 60+ putting them in the worst 5%. A risk score below 10 puts an organization in the best 10%.
Our scans found that 100% of clusters contained at least one misconfiguration, while 65% had at least one high-severity misconfiguration. 50% of clusters had 14 or more failed security controls. Here is a look at the top 5 misconfigurations found during our scans:
63% of the containers we scanned had one or more vulnerabilities, while 46% had one or more critical vulnerabilities. 53% had one or more RCE (Remote Code Execution) vulnerabilities. Here’s a look at the top 5 vulnerabilities that we found.
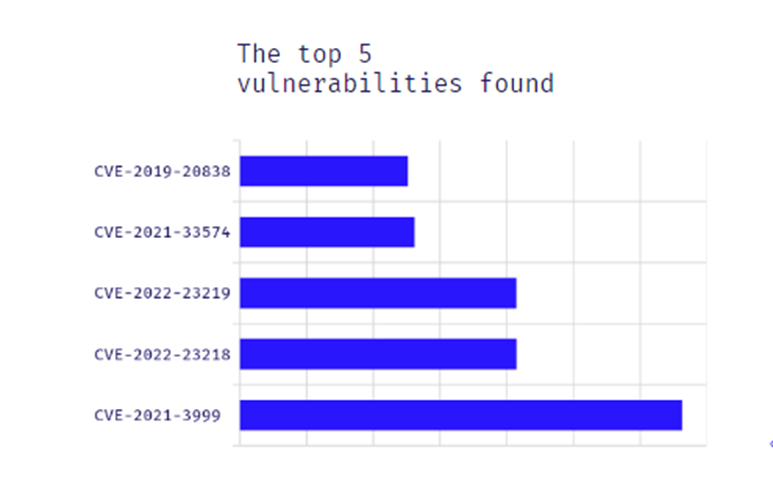
In all-
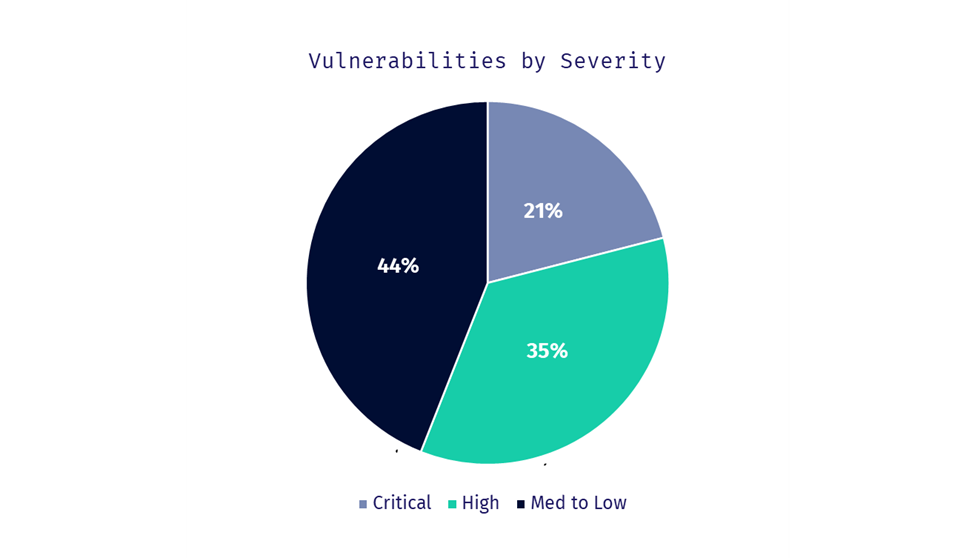
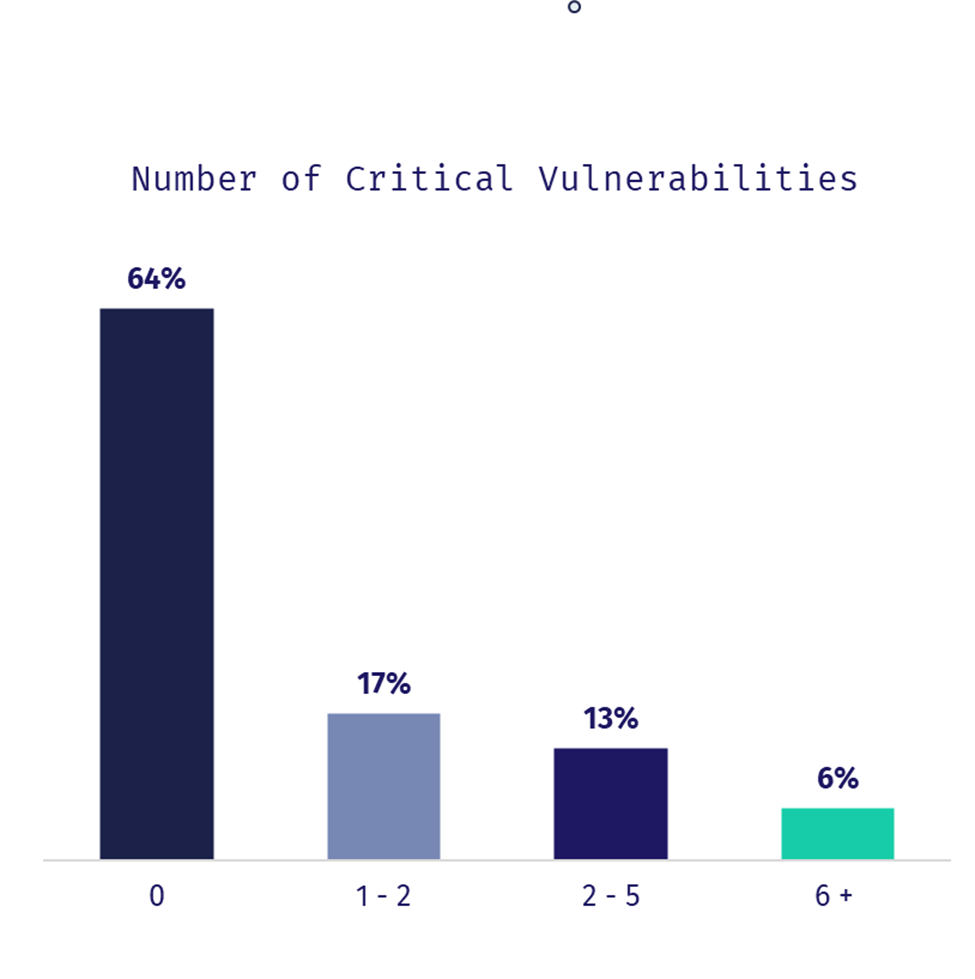
Even as organizations level up their cloud-native development and operations competencies, we still found misconfigurations in 100% of the scanned clusters. This demonstrates the importance of having the right security frameworks and tools in place to bolster the security posture of K8s implementations.

The only runtime-driven, open-source first, cloud security platform:
Continuously minimizes cloud attack surface
Secures your registries, clusters and images
Protects your on-prem and cloud workloads

Key Insights What is ADR (Application Detection & Response)? A security tool that monitors application-layer...

Key Insights What is a cloud workload protection platform (CWPP)? Security for the workloads actually...

The ARMO-Rapid7 partnership connects broad attack surface coverage with deep cloud and Kubernetes runtime security...