IngressNightmare: Analysis of Critical Vulnerabilities in Kubernetes Ingress NGINX Controller
Executive Summary On March 24, 2025, Wiz Research disclosed a series of critical vulnerabilities in...

Oct 28, 2022
This blog covers a developing story and it will be updated as new information and guidance become available. Please subscribe to The Kube-Blog By ARMO to get real-time updates (use the floating box).
OpenSSL is the most popular implementation of the TLS protocol (Transport Layer Security) which is essentially the de facto security protocol of the internet today.
The OpenSSL team announced critical security updates of versions above version 3.0 (OpenSSL 3.0 was released on September 7, 2021). The myriad of projects and software depending on OpenSSL must update and release a new version to enable end users to start patching their systems.
Few details of the vulnerability are currently available, but we want to warn you about the potential consequences.
The vulnerability is said to be on par with the severity of the infamous Heartbleed vulnerability which was found in 2014 (CVE-2014-0160) and enabled any attacker with network access to OpenSSL listening ports to extract sensitive information from the memory of the victim software which was based on OpenSSL.
The Heartbleed vulnerability required all software vendors to do an expedited release of their product. Users and operators had to rush and update live systems to mitigate the exposure.
In the Kubernetes ecosystem, any public-facing application will need to be reviewed. Especially Ingress controllers based on OpenSSL. The Kubernetes API server is not based on OpenSSL, therefore it is assumed that it is not vulnerable. We recommend you begin preparing for the upcoming releases and check the OpenSSL versions, especially Ingress controllers which are public internet-facing.
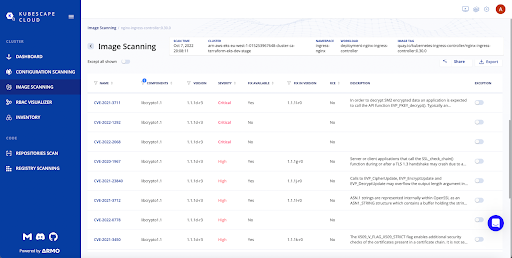
Kubescape Cloud continuously scans your applications and workloads to detect newly discovered vulnerabilities. Make sure you know about them in time by installing Kubescape in your clusters.
Using Kubescape cloud you can look for OpenSSL packages in your workloads and check if they are in the vulnerable range: Versions 3.0 – 3.06.
Executive Summary On March 24, 2025, Wiz Research disclosed a series of critical vulnerabilities in...

Imagine this situation: you recently updated one of your infrastructure software components. A few weeks...
In 2024, several significant vulnerabilities were identified within the Kubernetes and broader cloud-native ecosystem. In...