AI Security Posture Management (AI-SPM): The Complete Guide to Securing AI Workloads
Every cloud security vendor now has an AI-SPM dashboard. Strip away the branding, though, and...

Aug 6, 2024
We explored the Red Hat State of Kubernetes security report 2024, one of our favorite yearly reports. It’s jam-packed with incredibly fascinating information about one of our favorite subjects—Kubernetes security. Imagine that!
In this post we’ll review some of the more interesting data points and contrast them with results from prior years. We’ll also discuss our own perspectives and observations on how this affects you as a Kubernetes user. We will also show how ARMO Addresses 100% of Key Concerns Highlighted in the Report.
The following are perhaps the most important conclusions to draw from the data:
| 2024 | 2023 | 2022 | 2021 | |
| Have you ever delayed or slowed down application deployment into production due to container or Kubernetes security concerns? | ||||
| Yes | 67% | 67% | 55% | 55% |
| No | 33% | 33% | 45% | 45% |
| In the past 12 months, what security incidents or issues related to containers and/or Kubernetes have you experienced? | ||||
| Misconfiguration | 40%⬇ | 45% | 53% | 59% |
| Security incident during runtime | 45%⬇ | 49% | 30% | 32% |
| Major vulnerability to remediate | 44%⬆ | 42% | 38% | 31% |
| Failed audit | 26% | 27% | 22% | 20% |
| What is your biggest concern about your company’s container strategy? | ||||
| It isn’t taking security seriously or investing in security adequately | 42%⬆ | 38% | 31% | 45% |
| It is progressing too slowly | 19%⬇ | 25% | 22% | 15% |
| It doesn’t account for compliance needs | 14% | 14% | 6% | 14% |
| It doesn’t address skills gaps on our team | 11% | 13% | 20% | |
| It doesn’t account for cultural or process changes | 13% | 10% | 12% | |
| What role at your company is most responsible for container and Kubernetes security? | ||||
| Ops (architect, platform, infrastructure, SRE, cloud) | 18% | 20% | 16% | 21% |
| DevOps | 17% | 18% | 43% | 27% |
| DevSecOps | 15% | 15% | 19% | 18% |
| Security (cloud security, security eng., InfoSec) | 34%⬆ | 28% | 16% | 18% |
| Developer | 16% | 20% | 6% | 15% |
| Do you have a DevSecOps initiative in your organization? | ||||
| Yes – advanced stage | 42%⬇ | 45%⬆ | 27% | 25% |
| Yes – early stage | 48%⬆ | 39% | 50% | 49% |
| No | 10%⬇ | 17% | 22% | 26% |
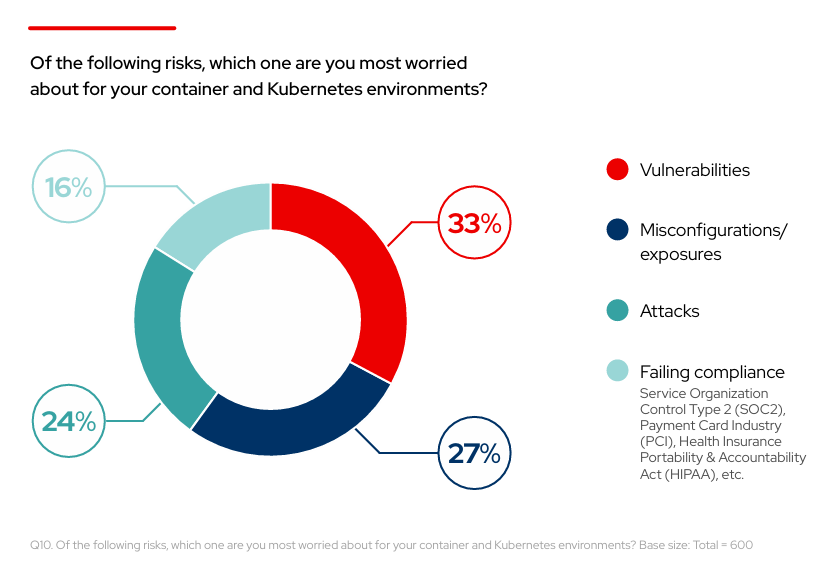
| Of the following risks, which one are you most worried about for your container and Kubernetes environments? | ||||
| Vulnerabilities | 33%⬆ | 30% | 28% | 31% |
| Misconfigurations/exposures | 27% | 28% | 46% | 47% |
| Attacks | 24% | 25% | 16% | 13% |
| Failing compliance (SOC2, PCI, HIPAA, etc.) | 16% | 18% | 9% | 8% |
ARMO is dedicated to addressing the genuine security concerns of businesses that use the cloud and specifically Kubernetes in production. It does so while mitigating alert fatigue in teams and inflated resource consumption, seen in some security tools. This dedication is demonstrated by ARMO Platform’s ability to address all issues highlighted in the report.
In summary ARMO covers 100% of the top risks that concern developers and security practitioners today with regards to Kubernetes security. Moreover, it is managed with a single pane of glass, and a holistic view that provides value to both security and DevOps practitioners.
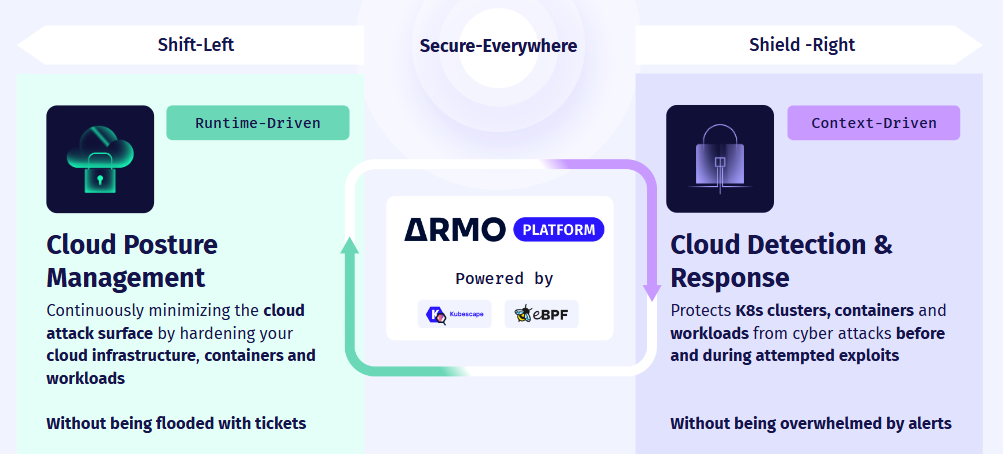
A fundamental technology that ARMO uses to create the context necessary to provide full coverage for all the security concerns detailed above is eBPF. It has developed an eBPF-based sensor that captures runtime information about the infrastructure and the application behavior. Combining that with cloud and Kubernetes context enables ARMO Platform to create a virtuous cycle.
It enables posture management to identify security gaps and risks during runtime. Runtime, in turn, signals there are emerging high-priority attack paths and provides context for vulnerability management. Runtime context also supports hardening measures without compromising application uptime and ensures continuous compliance.
The 2024 Red Hat State of Kubernetes Security report highlights several evolving trends and persistent challenges in the Kubernetes security landscape. Misconfigurations, while decreasing, remain a significant concern, alongside the rising worry about vulnerabilities. The data underscore the importance of continuous security scanning and the growing adoption of DevSecOps practices to foster collaboration between development and security teams.
ARMO’s approach to addressing these issues, through automated vulnerability management, misconfiguration alerts, and real-time attack detection, positions it as a solution of choice for organizations concerned with securing their Kubernetes environments. By leveraging advanced technologies like eBPF, ARMO ensures a holistic and proactive security posture, enabling businesses to mitigate risks effectively while maintaining operational efficiency.
As Kubernetes continues to be a cornerstone of modern infrastructure, the insights from this report serve as a vital guide for enhancing security strategies and safeguarding critical applications.
👉 Use this checklist to see where your Kubernetes security stands 👈

Every cloud security vendor now has an AI-SPM dashboard. Strip away the branding, though, and...

Your security stack was built for workloads that follow predictable code paths. AI agents don’t....

The Only Way to Secure AI in the Cloud AI is not just another workload...