What Is an Anomaly? Rethinking Runtime Detection in Cloud-Native Environments
“Anomaly detection” has become a core capability in modern cloud security. Yet despite its ubiquity...

Mar 4, 2025
Runtime security is all about real-time protection, actively monitoring and responding to threats as they happen, not just hardening, setting up barriers or reacting to attacks after the fact.
Think of it this way: traditional security measures prevent most intruders, but what about the ones that manage to get in? Runtime security alerts you to any suspicious activity and takes immediate action to stop it.
Why is this so important for containers? Containers are incredibly dynamic and powerful, but they also create larger attack surfaces, making them more vulnerable. Runtime security helps us address those vulnerabilities head-on, providing comprehensive protection.
Containerization has revolutionized application deployment and scaling, but it also introduces unique security challenges. Containers share the host operating system’s kernel, making them attractive targets for attackers seeking to exploit vulnerabilities or escalate privileges. Moreover, containers’ ephemeral nature can make traditional perimeter-based security controls less effective.
Runtime security solves this by providing continuous, real-time protection within containerized environments:
While we’ve only scratched the surface, it’s clear that runtime security is an important piece of the puzzle when it comes to securing containerized environments. Next we’ll explore the challenges and best practices for implementing it.
In exploring the world of runtime security in containerized environments, it’s clear we need a multi-layered approach.
Let’s examine the key components that comprise runtime security:
Security isn’t a one-time event, it’s a continuous process. We need to constantly monitor our containers, tracking everything from logs and performance metrics to resource utilization and network activity.
Runtime security solutions analyze the behavior of running applications against established baselines. They look for anything out of the ordinary – a sudden spike in network activity, an attempt to access sensitive data it shouldn’t, or a process behaving suspiciously. This vigilance can be powered by a combination of techniques:
This isn’t just about passively watching what’s happening in your containers. It’s about actively analyzing pertinent interactions, monitoring system calls as noted above, and data flowing in and out. We use tools like Intrusion Detection Systems (IDS) and Security Information and Event Management (SIEM) platforms to spot anomalies, which are deviations from the “normal” behavior of your applications.
Runtime-based responses allow us to take control in real-time by executing specific actions:
Stopping malicious activity is the next step. Once a threat is detected, runtime security tools need to act fast. This can involve automatically triggering policies when specific conditions are met, or leveraging well-defined playbooks to guide SOC operators through remediation steps like:
Taking immediate action is crucial during a security incident. Forensic analysis and root cause analysis are the next logical steps that drive long-term improvement. By thoroughly identifying the underlying causes of incidents, organizations gain valuable insights. These learnings strengthen defenses, enhance the organization’s overall security posture, and improve response capabilities for future incidents.
Runtime security is essential for containerized environments because it’s during application execution that threats truly come to life. These threats can be divided into three main categories: vulnerabilities within the containers themselves, vulnerabilities in the orchestration layer, and vulnerabilities specific to serverless architectures.
Let’s talk about container vulnerabilities first. One of the most worrisome is container escape. Attackers could exploit weaknesses in the way containers are isolated, essentially breaking out of their supposed sandbox and gaining access to the host system or even other containers. This opens the door to a whole range of nasty side-effects, from stealing data to taking complete control of the system.
Then there’s network intrusion, which can manifest as malicious traffic targeting containers. This could involve stealing data, disrupting communication, or even launching DDoS attacks. Runtime security solutions play a central role here by constantly monitoring the traffic flowing between containers and the host system, flagging anything suspicious.
Another major concern is code injection and memory corruption. Attackers can try to manipulate application code or memory using techniques like buffer overflows or code injection to execute their own commands or sneak in malware. This is why runtime security needs to be vigilant about analyzing and validating the code running within containers.
Now, let’s shift our focus to orchestrator vulnerabilities. Orchestration platforms like Kubernetes are powerful tools, but they also present attack surfaces. A prime example is API server exploitation. Attackers might find vulnerabilities in the Kubernetes API server, for example, that allows them to gain unauthorized access, modify configurations, or even take control of the entire cluster.
Similarly, node agent exploitation poses a serious threat. Node agents, like Kubelet, manage containers on each node. If attackers compromise these agents, they can gain a foothold on individual nodes, potentially spreading their influence across the entire cluster.
And let’s not forget that misconfigurations, while not vulnerabilities themselves, can be exploited by attackers. Incorrect settings or configuration drift within orchestration tools can be leveraged by attackers to bypass security measures, obtain privileged mode access levels, or exfiltrate data.
Finally, we have serverless vulnerabilities. These are unique challenges stemming from the nature of serverless computing. For instance, insecure API gateways can be exploited to gain unauthorized access to serverless functions, while injection attacks can be used to manipulate function behavior, leading to all sorts of problems. And vulnerabilities in the function invocation process could allow attackers to execute unauthorized actions or gain access to sensitive data.
Organizations confronting evolving cyber threats require a multi-layered protection. Runtime-informed vulnerability management to patch software weaknesses through targeted patching. Cloud security posture management (CSPM) to monitor and assess cloud infrastructure for misconfigurations. Kubernetes security posture management (KSPM) for continuous cluster security assessments. Cloud Application Detection and Response (CADR) for real-time threat identification and mitigation within cloud applications. Combining these layers creates a strong defense-in-depth strategy, that effectively safeguards runtime environments against a wide spectrum of cyber threats.
Continuously monitor application behavior – CPU and memory usage, network traffic, file system changes, and even process creations and terminations. Set up alerts for anything out of the ordinary, anything that indicates that something is not right, which is easier said than done.
But here’s the catch – you don’t want to drown in a sea of alerts. To avoid alert fatigue, leverage tools that prioritize alerts based on runtime context, correlate multiple incidents into a single, more meaningful event, and allow you to create automated response policies for certain threats. This way, you can focus on the real red flags while ensuring critical issues are addressed swiftly and efficiently.
Think of your containers like lightbulbs. When one burns out, you don’t try to fix them – you replace them. That’s the idea behind immutable infrastructure.
Embrace the concept of immutability. This approach centers on a structured change management process, emphasizing the “never modify in place” rule. Use read-only file systems for your containers. Whenever you need to update something, deploy a fresh container. Complement this with continuous scanning and monitoring to quickly identify vulnerabilities, misconfigurations and unauthorized tampering.
Remember, attackers are constantly evolving their tactics, so you need to stay one step ahead.
Instead of relying solely on signatures, which can be bypassed, implement behavioral analysis based threat detection at the runtime. These tools can spot suspicious activities like unexpected process execution, unusual network traffic, unauthorized file system access, and even privilege escalation attempts.
Keep your threat intelligence up-to-date. Integrate threat intelligence feeds into your security tools to get the latest information on emerging threats, known indicators of compromise (IOCs), and suspicious behaviors.
Don’t give your containers more privileges than they absolutely need. Apply the principle of least privilege – run containers as non-root users, limit their capabilities, and use namespaces and Linux security modules like AppArmor or SELinux profiles to tightly control access.
Container communication should be carefully managed and controlled. Define clear boundaries and protocols to ensure that interactions occur only within authorized channels, much like a secure network perimeter.
Use network policies to control container-to-container communication, limiting the attack surface and preventing lateral movement. In Kubernetes environments, leverage Pod Security Standards to set strict rules about what pods can do, limiting their capabilities and privileges.
Even with the best security measures in place, things can still go wrong. That’s why it’s smart to be prepared for the worst.
Regularly train your security teams on incident response procedures. Make sure they know their roles, responsibilities, and escalation paths. Document your procedures clearly and concisely, so everyone is on the same page in a crisis.
Remember, runtime security is a continuous process, not a one-time fix. You need to stay vigilant, adapt to evolving threats, and constantly refine your security posture.
We’ve discussed a variety of strategies to enhance security. These include runtime monitoring, setting up alerts, and embracing immutable infrastructure. Additionally, using specialized threat detection tools, minimizing container privileges, isolating workloads, and ensuring your incident response team is well-trained and ready to react quickly are crucial steps.
Don’t just react to security threats – stop them before they start. ARMO‘s proactive approach tackles vulnerabilities head-on with real-time security policy enforcement. ARMO Platform safeguards against critical threats like kernel exploits and container escapes, ensuring your containers remain secure.
Take control of your container security. Schedule a free demo of the ARMO platform today and experience advanced runtime protection.
“Anomaly detection” has become a core capability in modern cloud security. Yet despite its ubiquity...

Understanding Containerization and Container Runtime Containerization, a form of lightweight virtualization, lets applications inhabit their...
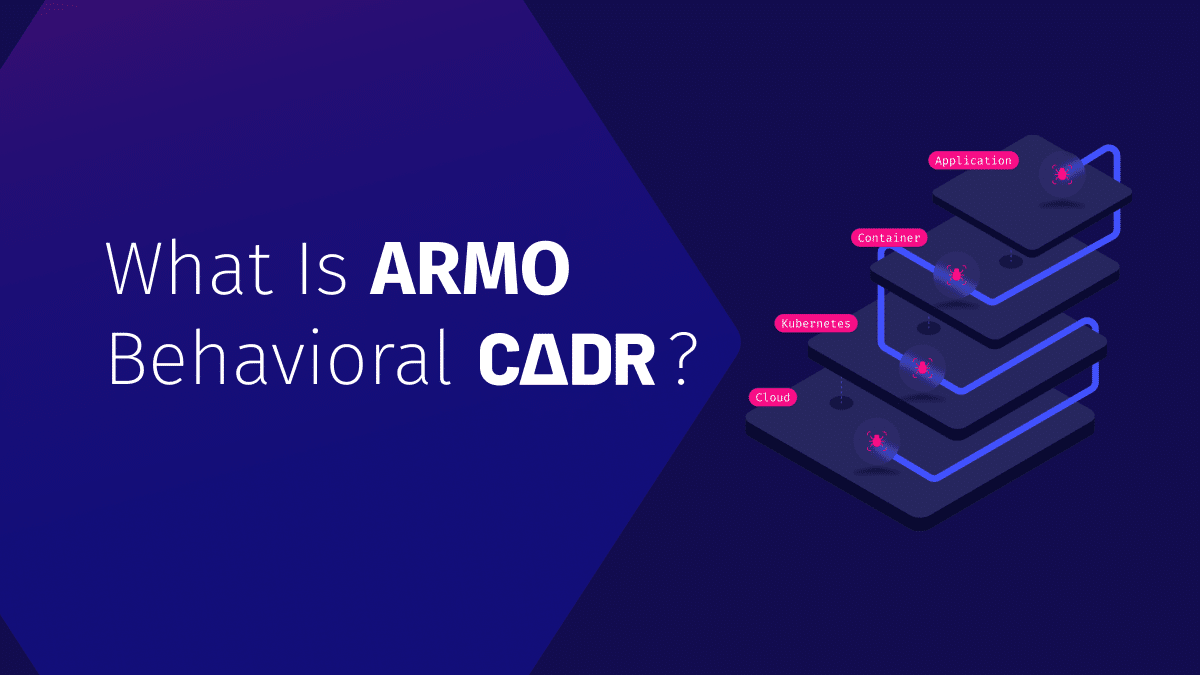
As organizations increasingly adopt cloud-native architectures, they face a sprawling attack surface with novel threats...