Software Supply Chain Security: A Detailed Explanation
Software supply chain attacks cost businesses $45.8 billion globally in 2023 alone, and is projected...
Feb 15, 2024
In an ideal world, patching every vulnerability before attackers discover them would be a breeze. The reality of the evolving cloud-native landscape, with its ever-changing mix of cloud, DevOps, mobile, and critical infrastructure, paints a different picture. New risks emerge constantly, leaving traditional vulnerability management approaches struggling to keep up. Meanwhile, Security and DevOps teams face ongoing pressure to protect their organizations from vulnerabilities.
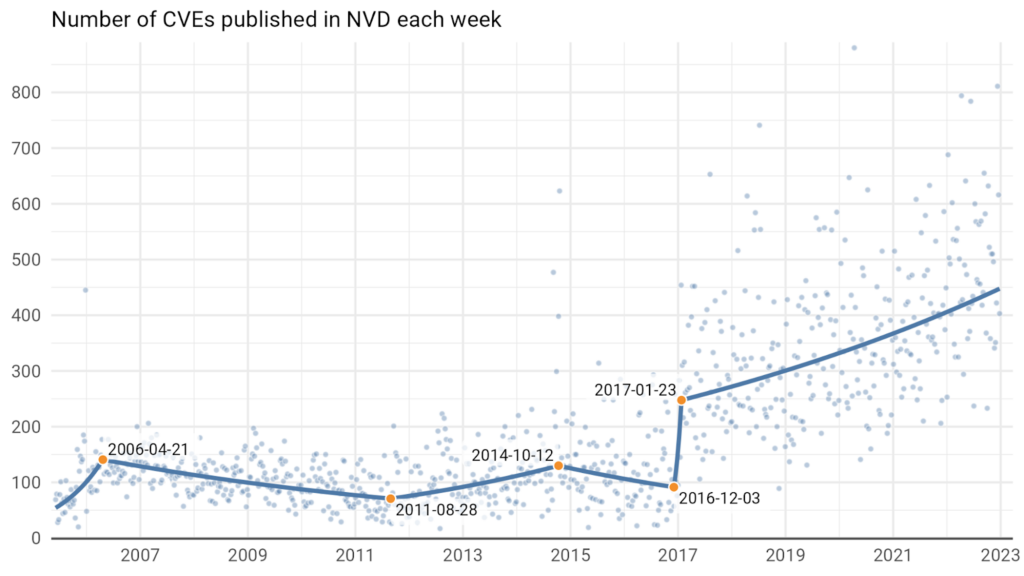
Over the past five years, there has been a significant surge in the number of identified Common Vulnerabilities and Exposures (CVEs), with researchers discovering over 110,000 new ones during that time alone. In fact, just last year in 2023, the highest annual figure was recorded, exceeding 29,000 CVEs. Managing such a vast number of vulnerabilities can be overwhelming for any security team, particularly without effective strategies for assessment, reporting, remediation, and ongoing monitoring.
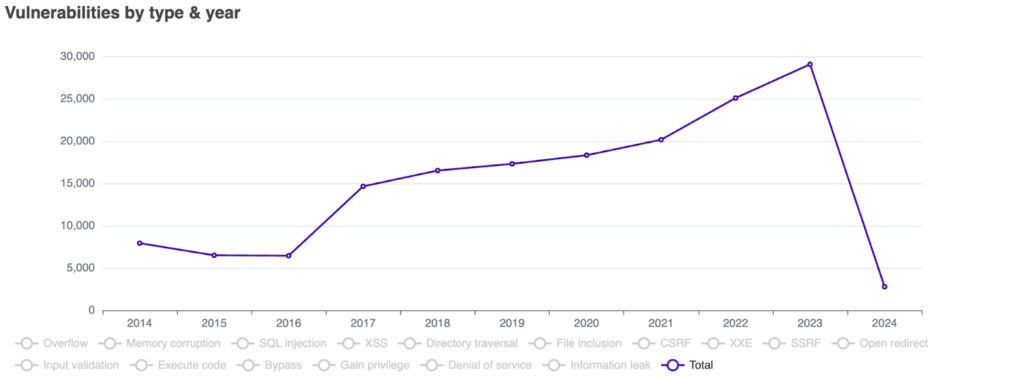
In cloud-native environments, it is crucial to adopt a runtime-based vulnerability management approach. ARMO introduced this concept in 2023 by utilizing Runtime Insights to focus users of ARMO Platform on actively used packages. This targeted approach effectively prevents alert fatigue which often arises from the constant flood of high-priority alerts generated through traditional scanners.
By optimizing vulnerability management processes, compliance and security teams are able to swiftly identify trends in risks while also tracking and reporting on them promptly. This empowers these teams to make well-informed decisions and strategically allocate resources instead of wasting time chasing after disparate vulnerabilities as they arise.
When it comes to vulnerability prioritization, Security teams often face these challenges:
1. Too many vulnerabilities to handle due to the constant discovery of new ones.
2. Relying solely on High and Critical CVSS scores is not effective, as many vulnerabilities don’t have working exploits.
3. Getting distracted by high-profile or zero-day vulnerabilities that might not pose actual risks.
Traditional vulnerability management often overwhelms security teams with a slew of vulnerabilities, making it challenging to prioritize resource allocation. However, runtime-based vulnerability management offers a solution by focusing on the critical 3% of vulnerabilities (source: ARMO based on anonymized production data) most susceptible to exploitation.
According to Gartner, addressing all vulnerabilities is the most impactful action for enhancing security. Despite efforts by many security teams to eliminate Critical and High vulnerabilities, the task has become more demanding. The scope of potential cyberattacks has broadened from traditional IT assets to encompass cloud services, DevOps, mobile apps, web infrastructure, and emerging devices like IoT equipment. This expansion complicates vulnerability management.
Getting a continuous, comprehensive view of the evolving attack surface, including diverse assets such as software containers, is a foundational challenge in cybersecurity. This is particularly crucial as cloud-native security requires a shift in how teams analyze and respond to threats.
Once security teams identify all vulnerabilities, another hurdle emerges: How to prioritize among the mass of vulnerabilities that fall into the category of Critical and High CVSS scores. The thing is that you don’t have to, not in the way many have been prescribing to date.
Traditional vulnerability management struggles to match the evolving landscape of the cloud-native attack surface. In contrast, runtime-based vulnerability management presents a more effective strategy. By targeting the 3% of vulnerabilities most susceptible to exploitation, it enables security teams to prioritize efficiently, allocate resources optimally, and increase the efficacy of vulnerability patching. This approach ultimately bolsters the organization’s security posture.If you’re ready to move beyond the constraints of traditional cybersecurity methods and adopt a smarter, more efficient approach to vulnerability management, explore ARMO Platform today.

The only runtime-driven, open-source first, cloud security platform:
Continuously minimizes cloud attack surface
Secures your registries, clusters and images
Protects your on-prem and cloud workloads

Software supply chain attacks cost businesses $45.8 billion globally in 2023 alone, and is projected...

Imagine this situation: you recently updated one of your infrastructure software components. A few weeks...
It is becoming increasingly important for organizations to manage Kubernetes security costs as they deploy,...