Kubernetes 1.34 – Top Security Enhancements 💪
Kubernetes v1.34 is coming soon, and it brings a rich batch of security upgrades –...

Oct 21, 2024
The dynamic world of Kubernetes and cloud security is constantly evolving. As we explore this complicated ecosystem, it’s crucial to understand the role of policy as code (PaC) and its impact on operations and security teams. Emerging from the broader paradigm of infrastructure as code (IaC), PaC represents a significant shift in how we manage and secure cloud-native environments.
In this blog post, we will explore the sophistication of implementing policy as code in Kubernetes, focusing on two key aspects: Seccomp profiles for container security and network policies for secure communications. We will also discuss the integration of GitOps in managing these policies, providing a comprehensive view of how these practices can fortify Kubernetes environments against emerging security threats.
Policy as code is a strategic approach integrating policy enforcement directly into the development and deployment pipeline. Similar to IaC with infrastructure resources, PaC streamlines the management of policies throughout the SDLC. The transition from IaC to PaC is a natural progression, enhancing teams’ capabilities to manage complex Kubernetes environments more effectively.
PaC is particularly beneficial in Kubernetes, where the dynamic and scalable nature of containerized applications can pose unique security challenges. There are many benefits to adopting this approach in Kubernetes:
In container security, seccomp (secure computing mode) is a critical feature for enhancing the safety and integrity of containerized applications. In this section, we will explore the origins, mechanics, and importance of seccomp profiles in the Linux kernel, particularly in the context of Kubernetes; we will also discuss how they contribute to creating a more secure computing environment.
Seccomp is pivotal in enhancing container security in the Linux kernel. Originally designed to restrict the system calls that a process can make, seccomp has evolved into a powerful tool for minimizing the attack surface of applications running in containers. By filtering system calls, it provides a sandboxing mechanism that can effectively isolate and protect containerized applications from various security threats.
In Kubernetes, seccomp profiles define the set of system calls containers can execute. This is integral to securing containerized applications, as it limits their access to the underlying host system, thereby reducing the risk of malicious exploits.
Seccomp profiles in Kubernetes are defined as JSON or YAML files, specifying the allowed and forbidden system calls for a container:
{
"defaultAction": "SCMP_ACT_ERRNO",
"architectures": [
"SCMP_ARCH_X86_64",
"SCMP_ARCH_X86",
"SCMP_ARCH_X32"
],
"syscalls": [
{
"names": [
...
"read",
"write",
"close",
... ],
"action": "SCMP_ACT_ALLOW"
}
]
}
When a container is deployed, the Kubernetes engine applies these profiles, ensuring that the container operates within the defined security parameters.
The technical implementation of seccomp in Kubernetes involves intercepting system calls made by the containerized application. If a system call is not explicitly allowed in the seccomp profile, it is blocked, thereby preventing potentially harmful operations in the runtime environment. This capability is crucial for ensuring container security.
Implementing seccomp profiles in Kubernetes requires a thoughtful approach to ensure both security and functionality. The following best practices are essential for effective seccomp profile deployment:
By integrating seccomp profiles into their Kubernetes security strategy, organizations can significantly enhance the security posture of their containerized applications, making them resilient against a wide range of cyber threats.
However, Kubernetes comprises a complex system with a larger attack surface, including but not limited to seccomp profiles. Make sure to read our blog Kubernetes Security Best Practices and Essential Protections for 2024 to learn more about ensuring a comprehensive security stance.
Due to the constant changes and interconnectedness that characterizes Kubernetes, network policies are key to the efficiency and security of network communications.
Network policies are Kubernetes resources that control traffic between pods and network endpoints. They are vital in orchestrating secure communication within the cluster. They establish a secure environment for pod-to-pod communication and access to external services.
By defining specific rules, network policies ensure that only authorized traffic can flow to and from pods, thereby significantly reducing the risk of network-based attacks.
Creating and implementing robust network policies in Kubernetes requires a strategic approach, focusing on defining clear and precise rules that align with your applications’ security and operational needs.
Network policies allow administrators to create rules that govern how pods within a Kubernetes cluster can communicate. Granular control over inter-pod traffic is enabled by defining rules based on pod labels, namespaces, specific network ports, or network policies.
Besides managing internal traffic, network policies can be configured to control how pods interact with external network endpoints. This includes defining rules for egress traffic from pods to external services and ensuring that only authorized and necessary connections are established.
Kubernetes Network Policies 101: a Brief Guide offers valuable insights and recommendations for crafting and implementing network policies.
Network policies in Kubernetes serve as a foundational element in securing containerized environments, ensuring a secure and resilient infrastructure for deploying and managing applications.
The combined approach of GitOps and PaC handles policies just like any other code and creates a seamless integration that we will explore in this section.
GitOps is a modern approach to managing Kubernetes in which Git serves as the definitive source for declaratively managing both infrastructure and applications. This methodology emphasizes the use of version control, automated deployments, and transparent operations, aligning closely with the principles of policy as code.
By integrating GitOps into Kubernetes management, teams can streamline the deployment, management, and enforcement of policies within their Kubernetes environments.
In the context of policy as code, GitOps plays a pivotal role. It enables teams to manage policies with the same rigor and precision as application code. Policies, defined as code, are stored in Git repositories, allowing for version control, peer reviews, and audit trails.
This approach ensures that any changes to policies undergo the same scrutiny and testing as application updates, thereby maintaining consistency and reliability.
Leveraging GitOps for policy management allows for continuous deployment and updates. When policies are updated in the Git repository, automation allows for these changes to be immediately applied to the Kubernetes environment. This ensures that the latest security and operational policies are always in effect while also minimizing the likelihood of human error and facilitating secure deployments.
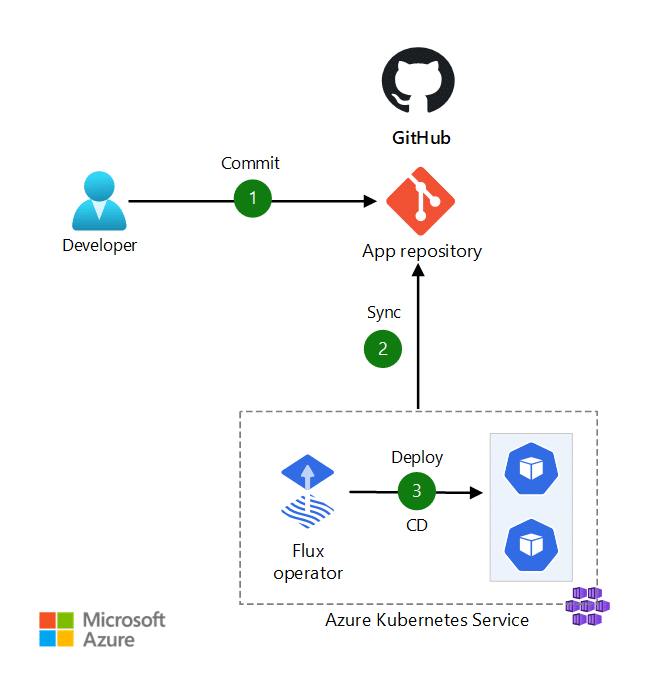
Integrating tools such as Terraform and Helm with GitOps further enhances the management of Kubernetes policies.
Terraform, an infrastructure-as-a-code tool, can be used to define and manage the underlying infrastructure for Kubernetes clusters. When integrated with GitOps, Terraform allows for the declarative specification of infrastructure and policies, ensuring the entire stack is version-controlled and reproducible.
An example network policy in Terraform is as follows:
resource "kubernetes_network_policy" "api_frontend" { metadata { name = "api-frontend-network-policy" namespace = "default" } spec { pod_selector { match_expressions { key = "name" operator = "In" values = ["api"] } } ingress { ports { port = "8125" protocol = "UDP" } from { namespace_selector { match_labels = { name = "frontend" } } } } ... } }
Helm, a package manager for Kubernetes, facilitates the deployment and management of applications and policies within Kubernetes. By using Helm charts, teams can package policies alongside applications, ensuring that the appropriate policies always accompany the deployment of applications.
Considering the customizability and reusability of Helm charts, integrating GitOps with PaC represents a powerful combination for managing Kubernetes environments. This synergy not only enhances the security and compliance of infrastructure but also brings a high level of efficiency and automation to policy deployment and management. And this, in turn, paves the way for more secure, scalable, and resilient Kubernetes ecosystems.
For more insights on integrating GitOps for Kubernetes security and compliance, make sure to read our blog discussing best practices and methodologies.
As we conclude our exploration of policy as code in Kubernetes, it’s clear that this approach is more than just a trend; it’s a fundamental shift in how we secure and manage cloud-native environments. The integration of seccomp profiles and network policies, underpinned by the principles of GitOps, represents a robust framework for enhancing the security posture of Kubernetes clusters.
ARMO Platform combines expertise in Kubernetes security with advanced tooling, its Network Policy and Seccomp Profile features provide a quick, easy and context aware way to implement policy as code effectively.
By embracing PaC and staying abreast of the latest trends and technologies, you can ensure your Kubernetes environments are not only efficient and scalable but also secure against today’s ever-changing landscape of cyber threats.
Kubernetes v1.34 is coming soon, and it brings a rich batch of security upgrades –...
At ARMO, our mission is to make Kubernetes security more accessible, actionable, and effective. That’s...

We’re excited to announce that ARMO now fully supports Google Kubernetes Engine (GKE) Autopilot clusters!...