Software Supply Chain Security: A Detailed Explanation
Software supply chain attacks cost businesses $45.8 billion globally in 2023 alone, and is projected...

Dec 26, 2022
Kubescape can now automatically scan Kubernetes clusters against the Center for Internet Security (CIS) benchmark, identify compliance gaps, suggest remediations, and monitor for drifts. This feature was born as a direct response to requests we received from Kubescape’s community and we’re excited to launch it. In this version, Kubescape supports CIS Kubernetes V1.23. In the next releases CIS GKE, AKS, and EKS frameworks will be supported as well.
The CIS Kubernetes benchmark is one of the leading frameworks used for compliance purposes and one of the most comprehensive security frameworks for Kubernetes, distilling best practices and standards into a rigorous set of checklists. This is why it is the security standard for many organizations and compliance implementations, including SOC2, HIPAA, PCI DSS, SRG, and NIST.
CIS benchmark gives you the ability to ensure that your security practices are up to date by checking:
Kubescape as a CIS benchmark tool, makes it easier than ever to scan Kubernetes and CI/CD pipelines using the CIS baseline. It helps provide clear, transparent guidance on how to fix failed controls and reach compliance. Kubescape exposes the root causes of security benchmark failures, and its assisted remediation also suggests how to fix the problems and harden Kubernetes so that the tests will pass at the next scan.
Kubescape has the ability to:
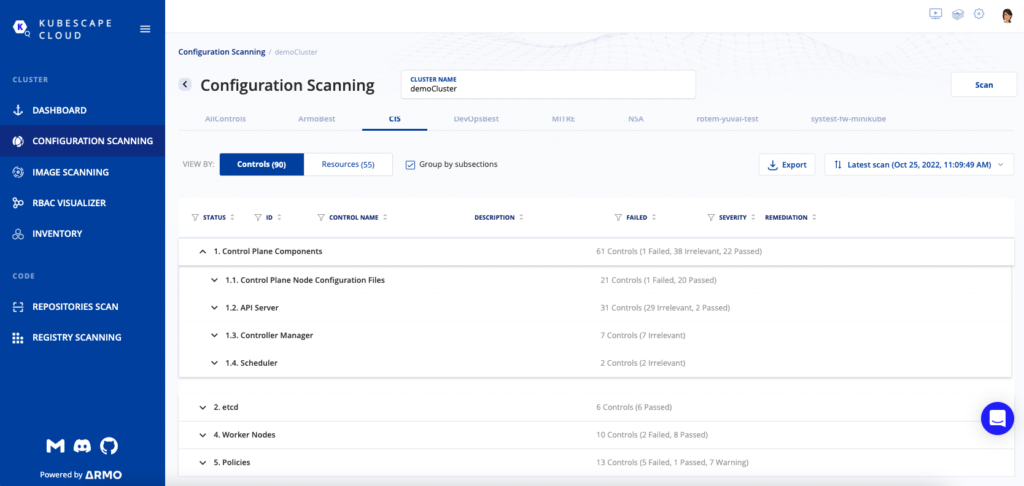
Kubescape calculates risk scores based on the CIS Kubernetes framework and tracks them over time to show how organizations are improving their security posture or drifting from standards. It can also generate reports based on the CIS framework for management, audits, and compliance certification such as SOC 2, PCI, NIST, HIPAA, and others. Uniquely, Kubescape is the only open-source solution that automates the entire process from scanning through remediation to reporting. Kubescape shows which CIS controls a Kubernetes infrastructure passes, which tests fail, and precisely what caused the failure.
As an example, let’s take a look at some security risks from CIS that came back on a Minikube cluster.
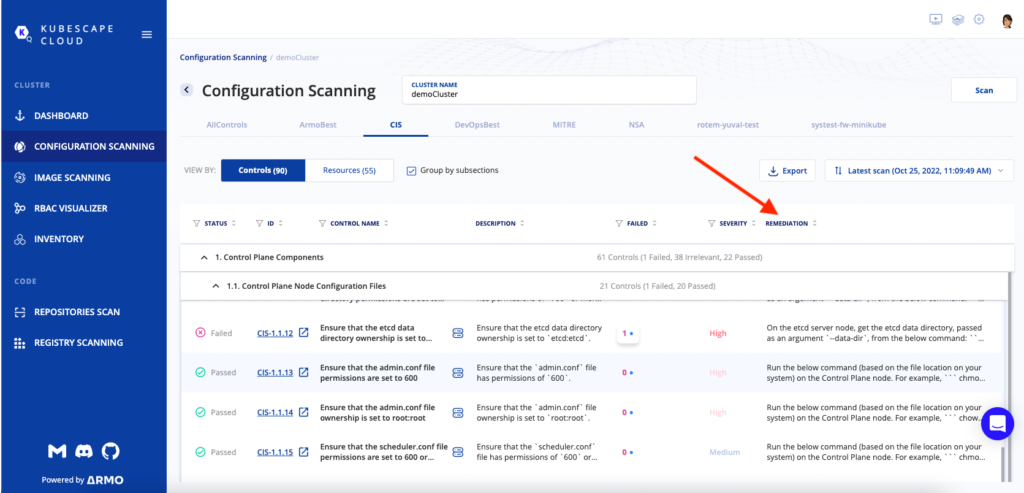
Once you see the remediation, you can highlight it or click it, and see the command that you should run based on the CIS recommendation.
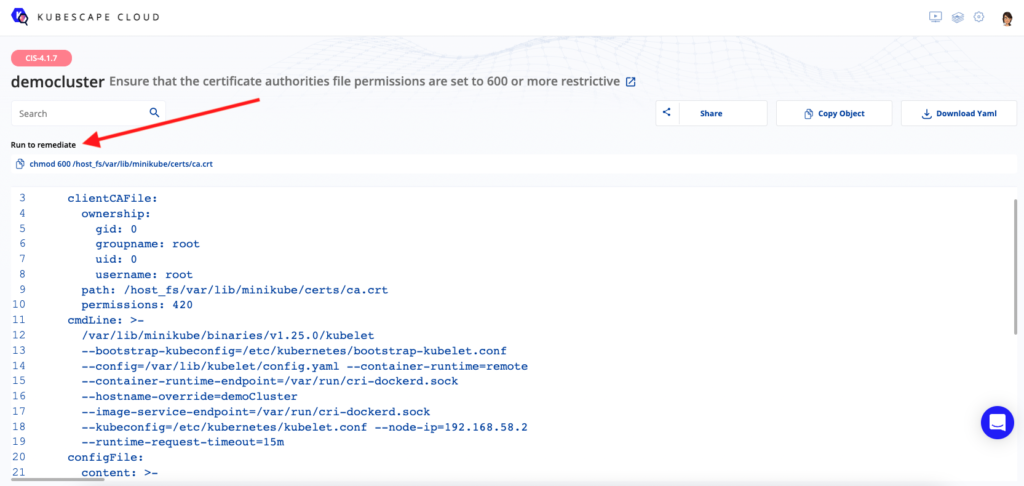
The reporting helps upper management and engineering leads understand what’s happening in a Kubernetes environment without having to go and do the scan themselves.
By clicking the Export button on the configuration scanner, you have three options.
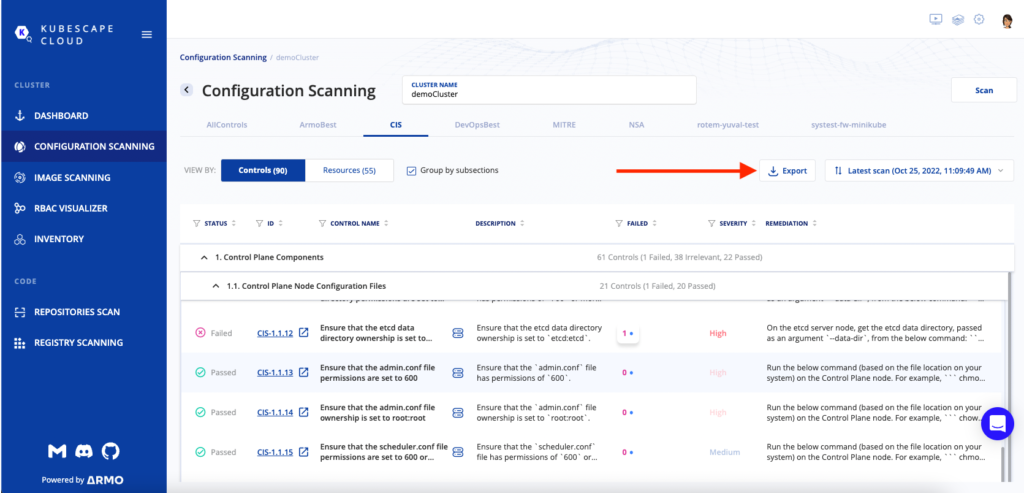
The three options are:
As an example, by clicking the Export Controls button, you can see that the output can be in an Excel spreadsheet and shared with management or other engineers on the team to understand what’s happening underneath the hood.
The CIS Kubernetes benchmark is supported by Kubescape alongside other security frameworks including NSA-CISA and MITRE ATT&CK®. Users can use all frameworks, choose just their preferred framework, or customize their own customized framework, choosing which controls to include or exclude from the scans. So go ahead, take this newly released feature for a ride, right now.

Software supply chain attacks cost businesses $45.8 billion globally in 2023 alone, and is projected...

We’re excited to announce that Kubescape has officially entered the CNCF Incubating stage! This achievement...

Imagine this situation: you recently updated one of your infrastructure software components. A few weeks...