ARMO named in Gartner® Cool Vendors™ report
We are excited and honored to announce that we were selected as Gartner Cool Vendor...
Jan 19, 2023
Transparency in vulnerability disclosure plays a crucial role in effective risk management, regardless of software development models. The Common Vulnerabilities and Exposures (CVE) database serves as a valuable resource, offering insights into known weaknesses even when fixes are unavailable. This empowers organizations to make informed decisions about prioritizing mitigation strategies and protecting their systems.
Vulnerability scoring systems rank CVE severity, with the Common Vulnerability Scoring System (CVSS) being the most popular. However, CVSS should not be considered the last word when it comes to vulnerability prioritization, as it focuses on severity and exploitability but lacks the necessary contextual and environmental information specific to different Kubernetes installations.
In addition, a holistic approach to risk management requires considering factors beyond CVSS, such as the dynamic nature of threats, real-world exploitability, and emerging vulnerability scoring systems (e.g., the Exploit Prediction Scoring System (EPSS) and Known Exploited Vulnerabilities (KEV) Catalog).
This article covers 2023 Kubernetes vulnerabilities, categorizing them based not only on CVSS but also weakness types, impact types, and other relevant factors. We will also broadly discuss the Common Weakness Enumeration (CWE) standards and best practices to stay informed.

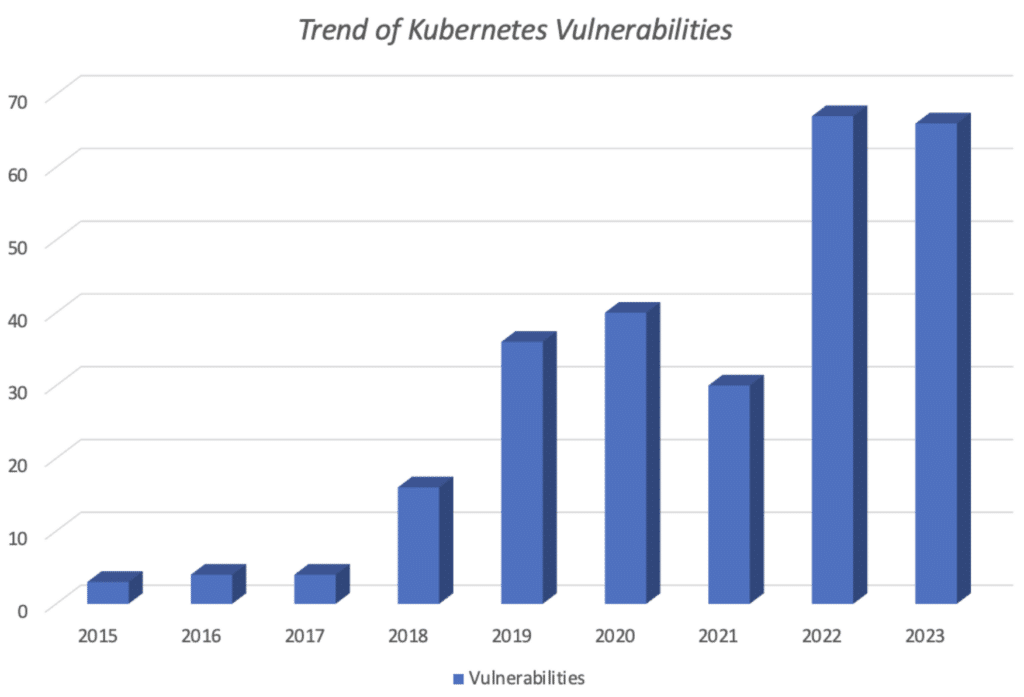
Despite its rapid growth, Kubernetes has never been regarded as secure by default, primarily because its vanilla clusters lack any default activation of security features such as network policies and pod security standards. Thus, the first step users must take is to activate Kubernetes-native security features. Between 2018 and 2023, there was a 440% increase in the number of vulnerabilities in Kubernetes. This does not indicate a decline in security but rather reflects a growing and expanding attack surface. As long as developers are writing software and expanding the ecosystem, we can expect to see more vulnerabilities.
According to the “State of Kubernetes Security report 2023,” 67% of respondents noted Kubernetes security concerns had forced them to delay or slow down deployments. Moreover, 90% reported having experienced one or more security incidents in the previous 12 months. Thus vulnerabilities are rising, primarily due to complicated vulnerability management processes and the expanding ecosystem around Kubernetes.
Before exploring vulnerabilities in-depth, let’s quickly review public databases and scoring systems for identifying, reporting, and prioritizing Kubernetes vulnerabilities.
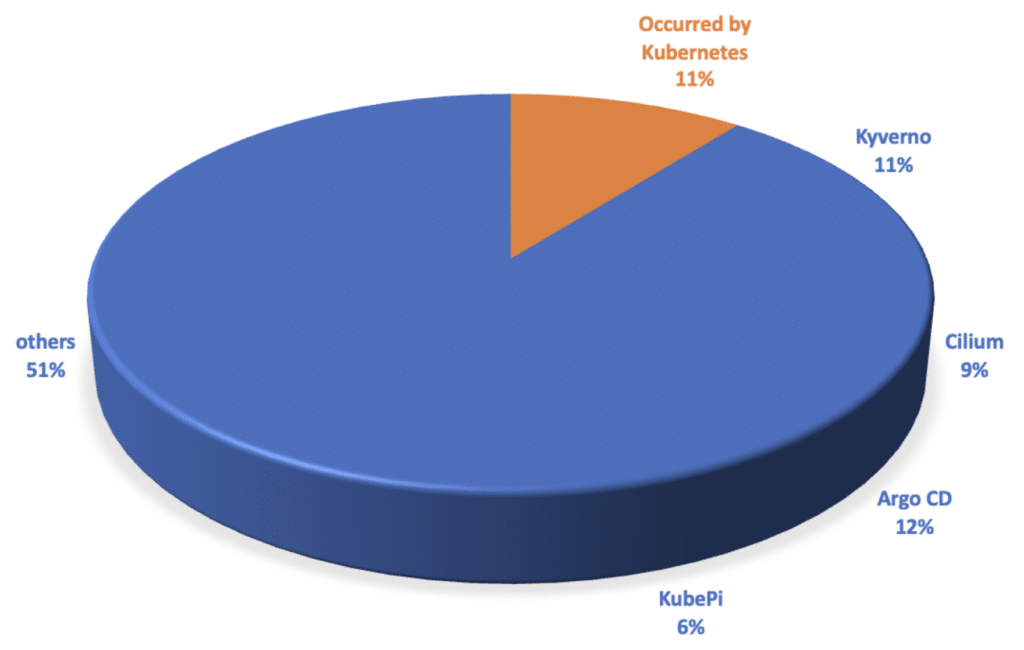
Out of the 66 known vulnerabilities, 59 were due to external tools used with Kubernetes, while only 7 were direct issues within Kubernetes itself. These vulnerabilities fall under two categories:
In this article, we examine and summarize all 7 known vulnerabilities in Kubernetes to help you monitor your Kubernetes clusters and mitigate potential security risks.
Users can escalate into admin privileges by creating pods or persistent volumes on Windows nodes.
All four of these vulnerabilities occur when a user on a Windows node, which has the ability to create pods or persistent volumes, elevates their privileges to an administrator level. These issues only affect clusters that employ an in-tree storage plugin for Windows nodes.
All of these vulnerabilities are rated 8.8 (high severity) by the NIST National Vulnerability Database and are significant for certain Kubernetes versions, namely those starting from 1.8.0, including all subsequent minor versions, are vulnerable. However, a patch was released on November 14, 2023, to fully address this issue.
Prevention and mitigation:
Users can launch containers and bypass the mountable secrets policy.
Normally, the mountable secrets policy is designed to ensure that pods using a service account can only access specified secrets in the service account’s secrets field. This is typically enabled by the ServiceAccount admission plugin.
This vulnerability specifically affects Kubernetes clusters that use both the ServiceAccount admission plugin and the kubernetes.io/enforce-mountable-secrets annotation with ephemeral containers. It is rated with a medium severity level, having a CVSS score of 6.5.
Prevention and mitigation:
Users are able to bypass container image restrictions.
Kubernetes usually employs the ImagePolicyWebhook to regulate which container images are permissible. This vulnerability allows users to launch containers with images that should be blocked by this control, but this only occurs when using ephemeral containers, which are temporary containers primarily used for troubleshooting.
This vulnerability affects Kubernetes clusters where both the ImagePolicyWebhook and ephemeral containers are used. It is rated as having a medium severity level with a CVSS score of 6.5.
Prevention and mitigation:
Pods can bypass the enforcement of the seccomp (secure computing mode) profile.
This security issue is identified in Kubelet and specifically affects pods that use the localhost type for the seccomp profile but have an empty profile field. In these instances, pods can run in an unconfined mode, meaning seccomp—which is designed to limit the system calls a container can make—is not enforced.
NIST has assessed this vulnerability with a medium severity level and a CVSS score of 5.5. However, the CVE Numbering Authority (CNA) has given it a lower score of 3.4.
Prevention and mitigation:
As shown in Figure 2, 89% of vulnerabilities originate from tools within the Kubernetes ecosystem. Notably, tools such as Kyverno, Cilium, AgroCD, and Kube Pi represent a significant source for these vulnerabilities. However, this does not necessarily indicate that these tools are inherently weak or flawed.
Vulnerabilities are common in a rapidly evolving ecosystem; the key is to proactively monitor for them and mitigate as necessary. Regularly scanning clusters for vulnerabilities, using tools like ARMO Platform, is essential to identify these vulnerabilities quickly and in the right context.
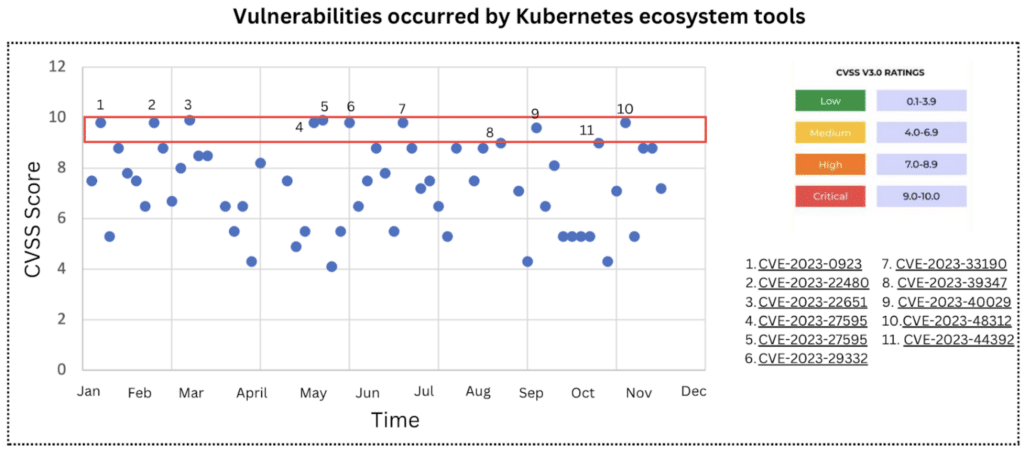
Figure 3 highlights vulnerabilities with high CVSS scores. In the Common Vulnerability Scoring System, critical vulnerabilities typically provide root-level access without needing special measures, such as authentication credentials. These vulnerabilities demand immediate attention, as they may enable attackers to fully control the system, steal data, or significantly disrupt operations.
Again, it’s important to note that the CVSS score should not be the sole measure of a vulnerability’s severity. CVSS lacks contextual information specific to particular environments or applications, as well as detailed information about exploitation in the wild. It is therefore recommended to follow a holistic approach to measure severity by considering the CVSS score as well as reachability and runtime data, while cross-referencing with other scoring systems.
This entails improper privilege management in SUSE Rancher.
Found in SUSE Rancher, an open-source container management platform, CVE-2023-22651 is a critical security vulnerability with a 9.9 CVSS score.
This vulnerability is particularly severe due to its high impact on privilege management, allowing for privilege escalation. This impacts users who have upgraded from Rancher versions 2.6.x or 2.7.x to 2.7.2. Notably, those who performed a fresh install of version 2.7.2 without following an upgrade path are not affected by this vulnerability.
The fundamental reason behind this problem is Rancher’s admission webhook update logic flaw. This webhook plays a crucial role in Rancher by enforcing validation rules and conducting security checks before resources being admitted into the cluster. The webhook can no longer effectively perform these validations when misconfigured due to the update logic failure. This lapse in security potentially creates opportunities for severe privilege escalations and data corruption, significantly compromising the overall security and integrity of the cluster.
Prevention and mitigation:
This entails improper authentication in Capsule Proxy, which leads to privilege escalation.
This is also identified as a critical vulnerability with a 9.8 CVSS score.
Capsule-proxy is a reverse proxy component used in the capsule operator project, which primarily functions in Kubernetes environments. This vulnerability arises because of a missing verification step to confirm if a user is authenticated. In particular, it impacts Kubernetes clusters where the anonymous-auth setting in the Kubernetes API Server is disabled (set to “false”).
anonymous_auth: # Disable anonymous authentication in Kubernetes API Server disabled: false # Set to true to disable anonymous access
In such scenarios, the token review mechanism can be bypassed, allowing unauthorized interaction with the Kubernetes API server and leading to potential privilege escalation.
Prevention and mitigation:
For proper categorization, we will be using CWE standards. This system classifies software flaws and vulnerabilities. It offers a consistent and quantifiable set of criteria for evaluating the severity of software issues and potential vulnerabilities. Maintained by MITRE, these standards are used by security practitioners to identify and categorize different types of vulnerabilities.
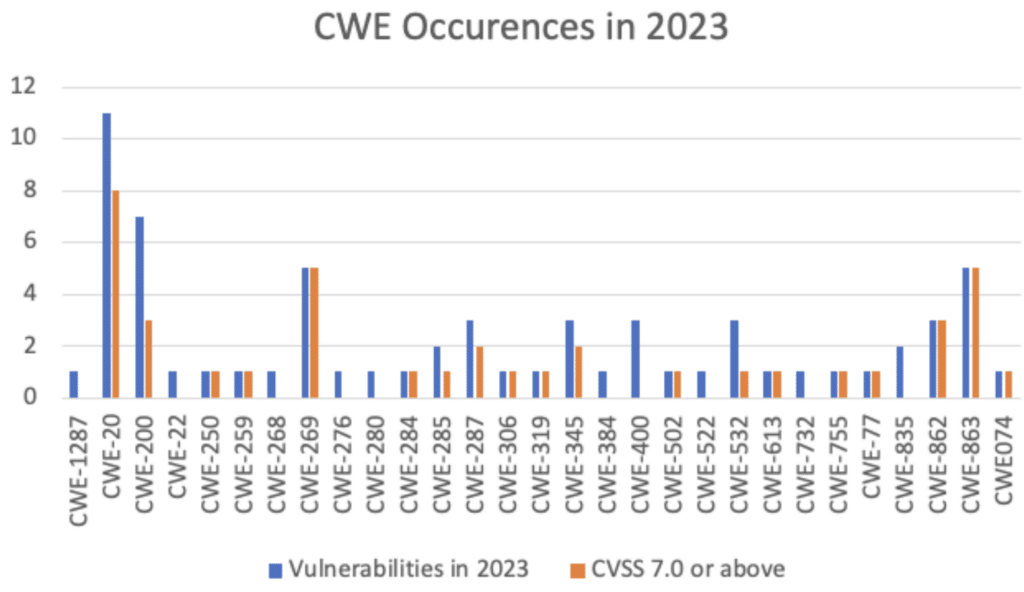
According to the analysis, these were the five most common types of vulnerabilities in 2023:
Understanding these exposure types is important to prevent and mitigate the most commonly occurring vulnerability types.
There are many ways to stay informed about vulnerabilities in your Kubernetes cluster. It is equally important to stay updated about common CWEs. In this section, we discuss key insights gained from a thorough analysis of all public vulnerabilities for the year 2023.
A persistent challenge in cybersecurity is that, no matter how secure a system is, vulnerabilities still exist. Skilled attackers will find ways to exploit these weaknesses. Therefore, being aware of ongoing vulnerabilities is essential. In the context of Kubernetes, there are several methods to keep up to date:
The Kubernetes community is highly active; if a vulnerability is publicly reported, typically, a patch is often provided within hours. Regularly applying patches and updates is therefore recommended. This also needs to be done fast, as hackers try to exploit disclosed vulnerabilities. Tools such as Ansible and Puppet can be instrumental in automating the deployment of these patches. Regular vulnerability scans based on CVE databases are also recommended. Organizations can use open-source tools such as Kubescape for scanning Kubernetes clusters and conducting risk assessments. Not only does Kubescape identify risks; it also offers guidance on remediation.
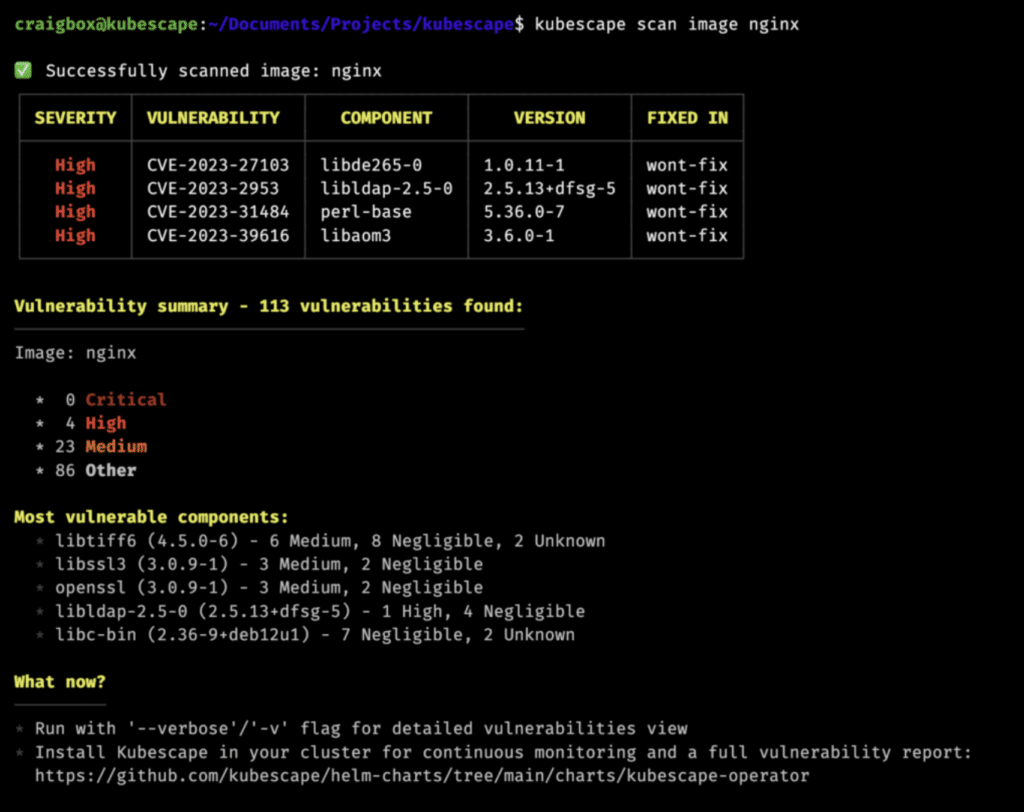
While addressing publicly identified vulnerabilities is common, there are rare instances of new types of vulnerabilities using previously unknown exploitation methods. In such cases, it is critical to have regular backups on hand and a disaster recovery plan in place. Tools such as Kasten K10 help to quickly restore data and resume normal operations. Finally, if the cluster or specific component is yet to be designed, attack surface reduction should be used to minimize unnecessary software and services running on your systems, thereby reducing the number of potential targets for hackers.
It is also advisable to leverage container isolation technologies like gVisor, which strengthens container security. These tools prevent container escape and unauthorized privilege elevation, providing solid isolation in multi-tenant environments. Such technologies are essential for enhancing container integrity and maintaining secure multi-tenant systems.
Managing risks effectively in Kubernetes environments requires a comprehensive security strategy that includes regular application of updates and patches, strict adherence to established k8s security best practices, and staying on top of emerging threats and vulnerabilities. Understanding and addressing common vulnerabilities, particularly those related to input validation and privilege management, is crucial for developing robust defense mechanisms.
While 2023 ended relatively quietly for cybersecurity professionals compared to years like 2020 and 2021, it’s vital to remember that cyber threats are constantly evolving. We can learn from past vulnerabilities like CVE-2021-44228 (Log4Shell), and the SolarWinds breach to maintain proactive vigilance in 2024.
With the growing complexity of attack surfaces, particularly in Kubernetes environments, prioritize effective identification and mitigation of security issues. Don’t wait for the next major incident – strengthen your Kubernetes security posture now with ARMO Platform. Its contextual vulnerability assessment cuts through the noise, reduces prioritization effort, and improves overall vulnerability management efficiency, letting you focus on what matters most. Secure your Kubernetes deployments and enjoy a year of proactive defense, not frantic reaction.

The only runtime-driven, open-source first, cloud security platform:
Continuously minimizes cloud attack surface
Secures your registries, clusters and images
Protects your on-prem and cloud workloads

We are excited and honored to announce that we were selected as Gartner Cool Vendor...
Discover the importance of mapping attack paths in Kubernetes and learn how to effectively enhance...

Learn about Kubernetes compliance challenges, consequences of non-compliance, and get guidance on maintaining a secure...