Software Supply Chain Security: A Detailed Explanation
Software supply chain attacks cost businesses $45.8 billion globally in 2023 alone, and is projected...

Jul 17, 2023
Kubernetes has emerged as the de facto standard for container orchestration, enabling organizations to manage and scale their applications efficiently. However, with this increased adoption comes the need to address security concerns within Kubernetes environments. The following blog post will explore the concept of ignoring security findings as a means of prioritizing fixes effectively.
Security findings are crucial in identifying vulnerabilities and risks within Kubernetes environments. These findings can range from misconfigurations to potential exploits. Left unaddressed, these can lead to unauthorized access, data breaches, or even system downtime. Therefore, organizations must take these findings seriously and allocate resources accordingly.
Prioritizing fixes in Kubernetes environments can be challenging due to several reasons:
Firstly, organizations often face staffing constraints where they must optimize their efforts based on available time and personnel. Secondly, the sheer volume of security findings generated by scanning tools can overwhelm teams responsible for remediation. Lastly, not all security findings are equally critical; some may have a low impact on your security posture while others require immediate attention.
Ignoring certain security findings can help address these challenges more efficiently. This allows organizations to focus on the critical issues that pose significant risks.
While ignoring specific security findings may enable efficient prioritization of fixes, there are both benefits and drawbacks associated with this approach.
The primary benefit is improved allocation of time and effort. This is because engineering time and effort can be redirected to address high-priority issues that directly impact system integrity and safety. By carefully analyzing and assessing risks, organizations can ensure that their engineering time makes a real impact. They can do this by filtering out non-critical or false-positive findings.
However, ignoring security findings does come with potential drawbacks. There is always the risk that what may initially seem insignificant could later be exploited by attackers or result in unforeseen consequences. Therefore, organizations must exercise caution and employ robust risk assessment mechanisms to avoid overlooking critical issues.
To safely ignore certain security findings without compromising security posture, organizations should adhere to the following best practices:
1. Develop a clear risk assessment framework: Establish an objective methodology for assessing the impact and likelihood of each security finding to determine its priority level accurately.
2. Update the risk assessment regularly: Continuously monitor and reassess ignored security findings as new information becomes available or threat landscapes evolve.
3. Maintain a comprehensive knowledge base: Document all ignored security findings along with justifications, ensuring transparency and accountability within the organization.
4. Foster collaboration between teams: Encourage cross-functional collaboration between development, operations, and security teams to gain diverse perspectives on prioritization decisions.
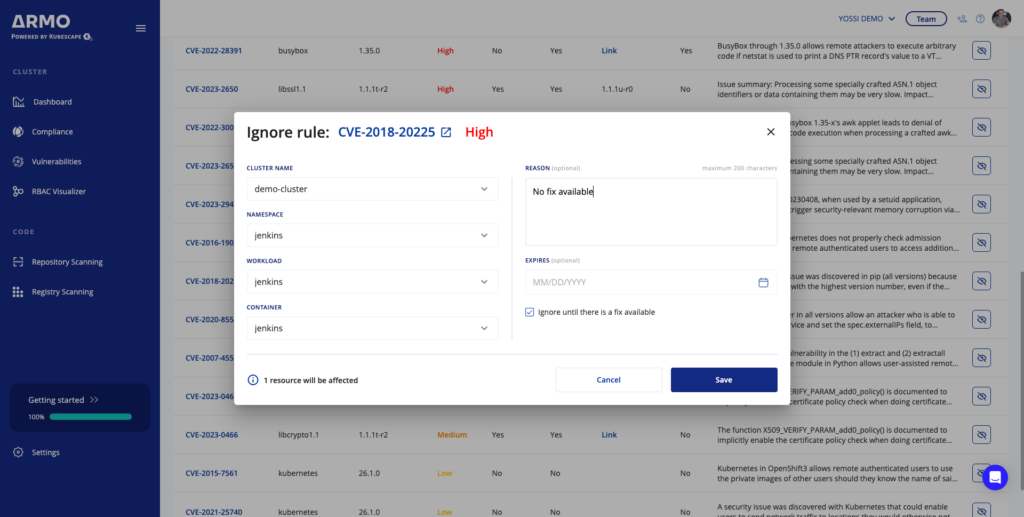
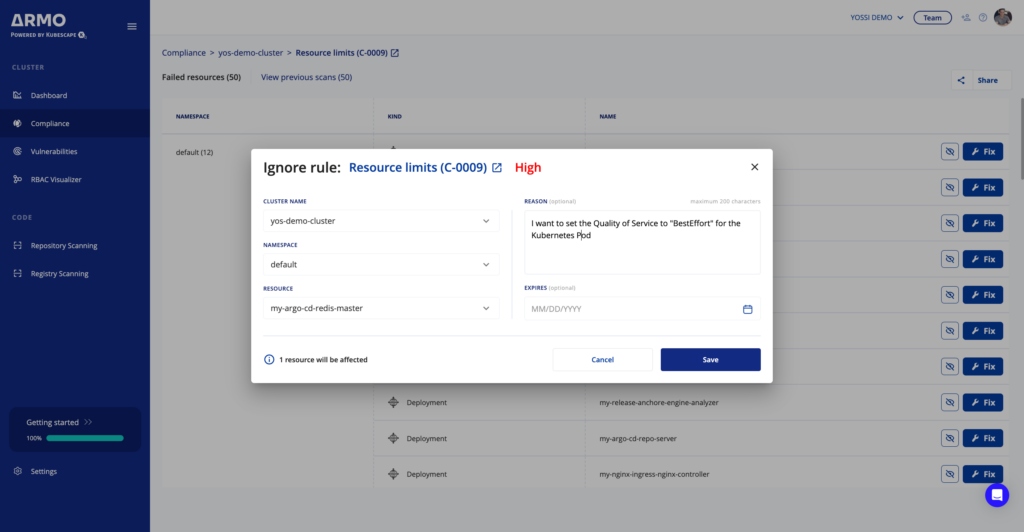
Prioritizing fixes in Kubernetes environments requires striking a balance between addressing all security concerns and efficiently managing resources. All with the goal of making a maximum impact on security posture. While it may be tempting to ignore certain security findings for efficient prioritization, you must carefully evaluate the risks associated with this approach. By adopting best practices such as clear risk assessments and continuous monitoring processes, you can ensure they make informed decisions about which security findings can be safely ignored without compromising system integrity or safety.
When managing Kubernetes security, you need to stay up-to-date on vulnerabilities and address them quickly. However, you also need to be mindful of engineering time and burden. By using the right tools and processes, you can maintain secure and resilient Kubernetes deployments that meet the needs of modern application architectures. ARMO Platform can help you do just that. If you’re not an ARMO Platform user yet, just sign up now (for free) and try for yourself.

The only runtime-driven, open-source first, cloud security platform:
Continuously minimizes cloud attack surface
Secures your registries, clusters and images
Protects your on-prem and cloud workloads

Software supply chain attacks cost businesses $45.8 billion globally in 2023 alone, and is projected...
As organizations increasingly adopt cloud-native architectures, they face a sprawling attack surface with novel threats...

Kubernetes security is an evolving challenge, and staying compliant with industry best practices is crucial....