Kubernetes v1.31 brings about some noteworthy improvements to the popular container orchestration platform that improve security and other aspects within the platform.
These enhancements improve account tokens, labeling, policies, and other areas to ensure a more secure and reliable platform for developers and enterprises.
Security-specific improvements in Kubernetes 1.31
The Kubernetes v1.31 introduces several security-related improvements that improve the overall security posture of the platforms and the workloads.
The AppArmor support enhancement (KEP-24) integrate AppArmor into Kubernetes, providing a way to enforce mandatory access control (MAC) policies for pods and containers.
AppArmor is a Linux security module that restricts programs’ capabilities through profiles, reducing the risk of security breaches. By allowing users to specify AppArmor profiles in Kubernetes manifests, this enhancement helps isolate and protect workloads, ensuring that even if an application is compromised, its ability to cause harm is limited by predefined security policies.
Key Aspects:
- Profile specification: Users can define AppArmor profiles in pod manifests.
- Profile enforcement: The specified profiles are enforced at runtime, restricting the capabilities of containers.
- Isolation: Enhances isolation between workloads, reducing the attack surface.
- Security: Helps mitigate potential damage from compromised applications by limiting their actions.
Benefits:
- Enhanced security: By restricting what applications can do, even if compromised.
- Granular control: Provides fine-grained control over container permissions.
- Compliance: Helps meet security compliance requirements by enforcing strict access controls.
Implementation details:
- Annotations: AppArmor profiles are specified using annotations in pod definitions.
- Profile management: Administrators need to manage and maintain AppArmor profiles on the nodes.
Compatibility: Requires underlying node support for AppArmor.
apiVersion: v1
kind: Pod
metadata:
name: sample-pod
annotations:
container.apparmor.security.beta.kubernetes.io/container-name: localhost/profile-name
spec:
containers:
- name: container-name
image: sample-image
For more detailed information, please visit the KEP-24 issue page.
This Kubernetes enhancement enhances the security of pulling container images that require secrets, such as private registry credentials. The key goal is to ensure these secrets are securely managed and used during the image-pulling process, mitigating risks associated with unauthorized access to sensitive data.
Key aspects:
- Secure secret management: Ensures secrets used in image pulls are managed securely.
- Access control: Implements access controls to prevent unauthorized access to these secrets.
- Auditing and logging: Enhances auditing and logging to track secret usage and access.
Benefits:
- Improved security: Reduces the risk of unauthorized access to private images.
- Compliance: Helps meet security and compliance requirements by securely handling secrets.
- Visibility: Provides better visibility into secret usage and potential security issues.
Implementation details:
- Kubelet enhancements: Modifies Kubelet to securely handle secrets during image pulls.
- Secret distribution: Ensures secrets are distributed securely to nodes and used appropriately.
- Configuration: Administrators can configure policies to manage how secrets are handled during image pulls.
apiVersion: v1
kind: Pod
metadata:
name: example-pod
spec:
containers:
- name: example-container
image: private-registry.example.com/my-image
imagePullSecrets:
- name: my-registry-secret
For more detailed information, please visit the KEP-2535 issue page.
This Kubernetes enhancement improves security by restricting anonymous authentication to only specific, pre-configured endpoints. It aims to reduce the risk associated with unrestricted anonymous access, which could be exploited by malicious users.
Key Aspects:
- Controlled access: Limits anonymous access to specific, safe endpoints only.
- Configuration: Administrators can define which endpoints allow anonymous access.
- Security: Enhances overall cluster security by minimizing the potential attack surface.
Benefits:
- Enhanced security: Reduces unauthorized access risks.
- Compliance: Helps in meeting security compliance requirements.
- Granular control: Provides fine-grained control over endpoint access.
Implementation details:
- API server configuration: Changes in the API server to support this functionality.
- Endpoint management: Administrators specify endpoints in configuration files.
For more detailed information, please visit the KEP-4193 issue page.
This enhancement aims to improve the security and usability of bound service account tokens in Kubernetes. These tokens are used to authenticate pods to the Kubernetes API server and other services. The goal is to enhance their lifecycle management, rotation, and revocation, addressing security issues associated with long-lived tokens.
Key Aspects:
- Token bound to pods: Tokens are closely tied to the pod’s lifecycle, ensuring they are valid only as long as the pod exists.
- Automatic rotation: Tokens are automatically rotated, reducing the risk of misuse if a token is compromised.
- Revocation: Enhances the ability to revoke tokens when they are no longer needed.
Benefits:
- Improved security: Reduces risks associated with long-lived and stale tokens.
- Ease of use: Simplifies token management for developers and operators.
- Compliance: Helps meet security compliance requirements by ensuring robust token management.
Implementation details:
- TokenRequest API: Introduces a new API to request tokens that are bound to the pod’s lifecycle.
- Shorter token lifetimes: Configures tokens to have shorter lifetimes, with automatic renewal mechanisms.
- Revocation mechanisms: Provides mechanisms to revoke tokens when they are no longer needed or when the pod is terminated.
apiVersion: v1
kind: Pod
metadata:
name: example-pod
spec:
serviceAccountName: example-service-account
containers:
- name: example-container
image: example-image
For more detailed information, please visit the KEP-4193 documentation.
This enhancement aims to improve the security and flexibility of the Kubernetes API server by supporting out-of-process JSON Web Token (JWT) signing. This allows the API server to delegate the responsibility of signing tokens to an external process or service, enhancing security and scalability.
Key aspects:
- External JWT signing: Allows the Kubernetes API server to use an external process for signing JWTs.
- Increased security: Reduces the risk associated with the API server handling private keys directly.
- Scalability: Enhances scalability by offloading token signing to a specialized service.
Benefits:
- Enhanced security: Isolates the signing process, reducing the attack surface.
- Flexibility: Allows integration with external identity providers and signing services.
- Improved management: Simplifies key management and rotation processes.
Implementation details:
- Configuration: Administrators configure the API server to delegate JWT signing to an external process.
- External signing service: The external service must implement a specific API to handle signing requests.
For more detailed information, please visit the KEP-3908 documentation.
This enhancement introduces the ability to use field and label selectors in authorization policies, allowing for more granular access control in Kubernetes. By enabling these selectors, administrators can define precise rules based on resource fields and labels, improving the flexibility and security of the access control system.
Key Aspects:
- Field selectors: Allows authorization policies to use resource field values.
- Label selectors: Enables the use of resource labels in access control decisions.
- Granular access control: Provides finer control over who can access specific resources.
Benefits:
- Enhanced security: Reduces over-permission by allowing precise access control.
- Flexibility: Supports complex policies based on resource attributes.
- Improved management: Simplifies the creation of detailed and specific authorization rules.
Implementation details:
- Policy definition: Administrators can define policies using field and label selectors.
- API server changes: Modifications to the API server to support these selectors in authorization checks.
For more details, visit the KEP-4601 documentation.
This enhancement aims to introduce mutating admission policies in Kubernetes, providing a flexible way to modify requests to the API server. These policies are evaluated and applied before the requests are persisted, enabling dynamic modification of resources based on custom criteria.
Key aspects:
- Dynamic modification: Allows the modification of API requests before they are persisted.
- Custom policies: Supports custom criteria for modifying requests.
- Flexibility: Enhances the flexibility of Kubernetes admission control.
Benefits:
- Enhanced control: Provides fine-grained control over API requests.
- Customization: Allows administrators to define custom logic for modifying resources.
- Improved security: Ensures that requests meet specific policies before being accepted.
Implementation details:
- Policy definition: Administrators define mutating policies using CustomResourceDefinitions (CRDs).
- Admission webhooks: Utilizes mutating admission webhooks to apply the defined policies.
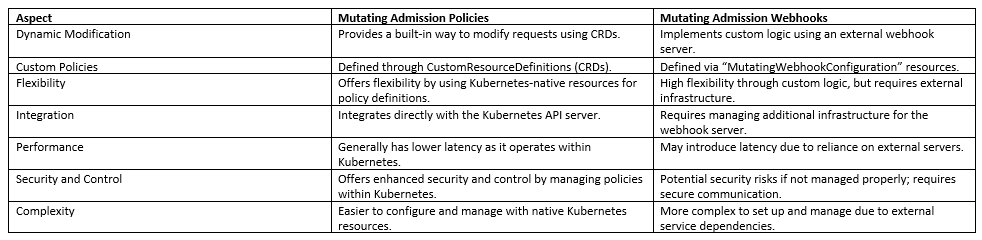
Mutating admission policies Vs mutating webhooks
Mutating Admission Policies and Mutating Admission Webhooks in Kubernetes both serve the purpose of modifying requests to the API server before they are persisted. However, there are distinct differences in how they operate and their flexibility. The following table shows a comparison between the two.
Conclusion
Kubernetes v1.31 brings several enhancements that significantly improve security, scalability, and developer experience within the platform. Key takeaways include:
- Enhanced Security Mechanisms: Integrations such as AppArmor support (KEP-24) for mandatory access control, improved management of secret-pulled images (KEP-2535), and restrictions on anonymous authentication (KEP-4633) enhance the security of workloads and data within Kubernetes.
- Improved Token Management: Enhancements to bound service account tokens (KEP-4193) ensure better lifecycle management, rotation, and revocation, reducing risks associated with long-lived tokens.
- Advanced Authorization Control: Features like out-of-process JWT signing (KEP-3908) and authorization with selectors (KEP-4601) provide more granular and flexible access control and security measures.
- Flexible Admission Policies: The introduction of mutating admission policies (KEP-3962) allows for dynamic modification of API requests, enhancing control over resource configurations and security.
These updates underscore Kubernetes’ commitment to advancing its security and usability, making it a more secure and reliable platform for developers and enterprises. For more details, visit the respective KEP issue pages and documentation.