Cloud Security Posture Management (CSPM) has become essential for monitoring cloud infrastructure, identifying risks, and enforcing security policies. As cloud adoption grows, managing the complexity of these environments—where misconfigurations and vulnerabilities can lead to breaches—requires a robust approach. This is where security frameworks come into the picture.
Security frameworks offer structured guidelines and best practices for managing and improving security posture. They cover key areas like risk management, compliance, and threat detection. By aligning CSPM strategies with these frameworks, organizations can reduce security risks and meet industry standards.
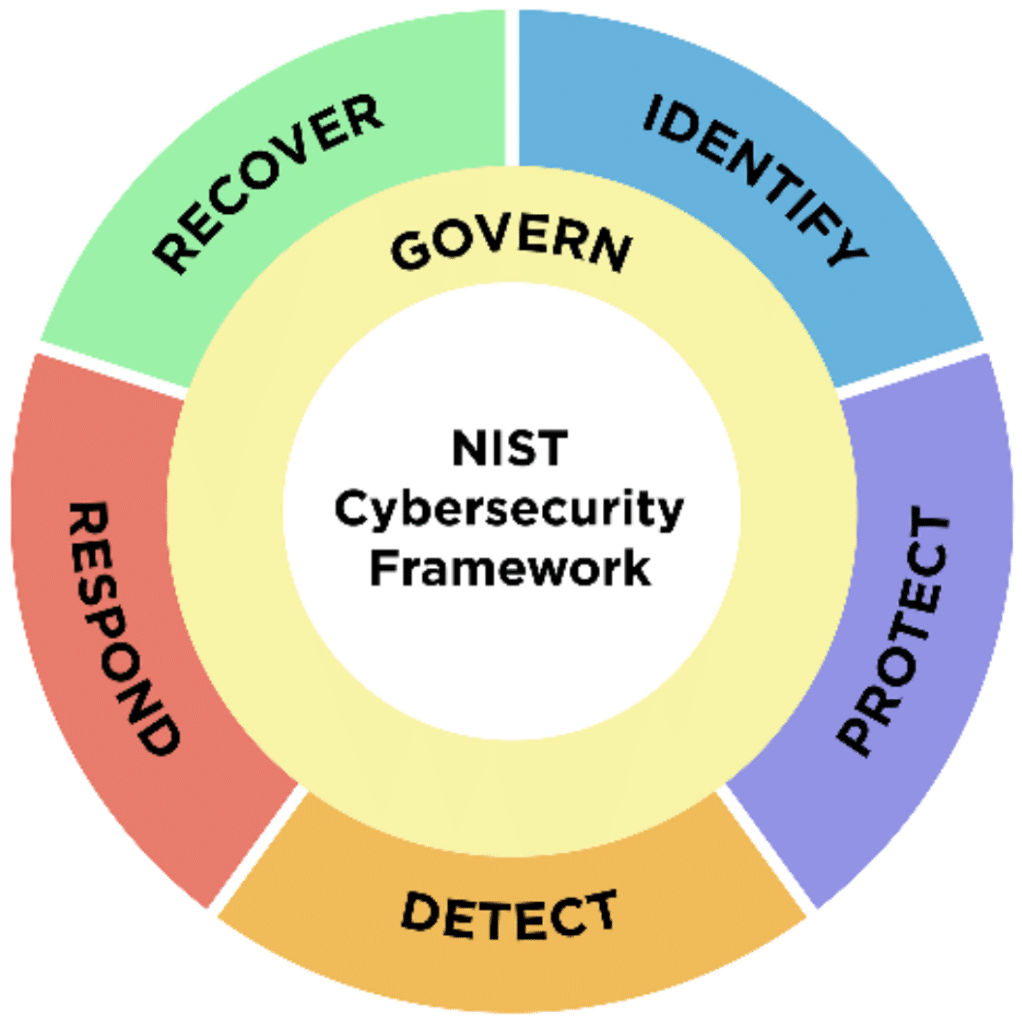
For example, the NIST Cybersecurity Framework (CSF) provides core functions—Identify, Protect, Detect, Respond, and Recover—to manage cybersecurity risks. Similarly, the Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM) offers security controls specific to cloud environments, covering areas such as access management and data protection.
Incorporating these frameworks into CSPM is essential in today’s evolving threat landscape. This article explores leading security frameworks that can be integrated with CSPM to strengthen cloud security efforts.
Quickly ensure your Kubernetes is secured.
Follow this simple checklist and make sure your Kubernetes security is covered in just a few steps.
Read Now
Understanding Security Frameworks
Security frameworks are structured guidelines, standards, and best practices designed to help organizations manage cybersecurity risks systematically. These frameworks provide a comprehensive approach to identifying, protecting, detecting, responding to, and recovering from security incidents. They are not one-size-fits-all solutions but rather adaptable tools that can be tailored to meet an organization’s specific needs, particularly in cloud environments.
The primary purpose of a security framework is to create a consistent and repeatable process for managing security risks. This includes defining security policies and procedures, implementing technical controls, and conducting regular audits. In the context of Cloud Security Posture Management (CSPM), these frameworks help ensure that cloud resources are configured securely, monitored continuously, and compliant with industry regulations and organizational policies.
Key Components of Security Frameworks
- Policies and Procedures: Formal documents that outline security requirements, roles, and processes. For example, a policy might require encryption for all cloud resources, while a procedure details how to audit configurations regularly.
- Controls: Technical or administrative measures to mitigate security risks. In cloud environments, controls include access management, encryption, logging, monitoring, and automated compliance checks, such as enabling Multi-Factor Authentication (MFA).
- Risk Management: Identifying, assessing, and prioritizing risks, followed by implementing controls to mitigate them. This might involve regular vulnerability assessments and using CSPM tools to detect and remediate misconfigurations in real-time.
- Compliance Requirements: Guidelines to meet regulatory or industry standards like GDPR, HIPAA, or PCI DSS. CSPM tools monitor cloud environments for compliance, generating reports to highlight deviations.
- Continuous Monitoring and Improvement: Ongoing monitoring to detect and respond to incidents as they occur, is crucial in dynamic cloud environments. Frameworks also promote continuous improvement to adapt to emerging threats.
How Frameworks Enhance CSPM
Security frameworks enhance CSPM by offering a structured approach to managing cloud security:
- Standardization: Frameworks ensure a consistent approach, reducing misconfigurations and security gaps.
- Compliance: Aligned with regulatory standards, frameworks help maintain compliance. CSPM tools automate compliance checks, easing the burden on security teams.
- Risk Reduction: Frameworks provide a proactive approach to identifying and addressing cloud security risks. CSPM tools support this by continuously scanning for vulnerabilities.
- Incident Response: Frameworks offer guidelines for detecting and responding to incidents, which, when integrated with CSPM, can automate and improve incident response.
Leading Security Frameworks for CSPM
1. NIST Cybersecurity Framework (CSF)
The NIST Cybersecurity Framework (CSF) is a widely recognized framework that provides organizations with a structured approach to managing and reducing cybersecurity risks. Developed by the National Institute of Standards and Technology (NIST), the framework is built around five core functions: Identify, Protect, Detect, Respond, and Recover. These functions guide organizations in managing their security posture comprehensively.
Core Functions:
- Identify: Focuses on understanding the organization’s assets, risks, and resources. In CSPM, this includes identifying cloud assets, understanding the security requirements, and assessing risks.
- Protect: Involves implementing safeguards to ensure the delivery of critical infrastructure services. For CSPM, this means applying security controls such as encryption, access management, and configuration management.
- Detect: Covers the activities needed to identify cybersecurity events in a timely manner. CSPM tools integrate with the Detect function by continuously monitoring cloud environments for misconfigurations, vulnerabilities, and suspicious activities.
- Respond: Focuses on taking action after a security event has been detected. CSPM tools can automate incident response actions, such as isolating compromised resources or initiating remediation workflows.
- Recover: Supports timely recovery to normal operations. In CSPM, this can include restoring cloud configurations from secure backups and ensuring that lessons learned from incidents are integrated into future prevention strategies.
2. CIS Critical Security Controls (CIS Controls)
The Center for Internet Security (CIS) Critical Security Controls (CIS Controls) is a set of prioritized actions designed to defend against the most common cyber threats. The controls are categorized into Implementation Groups (IG1, IG2, IG3) based on the organization’s size, complexity, and risk exposure.
Implementation Tiers:
- IG1 (Basic): Focuses on essential cyber hygiene, such as inventory management, secure configuration, and access control. For CSPM, this involves ensuring that all cloud assets are identified and that security configurations are enforced.
- IG2 (Foundational): Builds on IG1 by adding more controls like vulnerability management, secure application development, and incident response. CSPM tools automate the detection and remediation of vulnerabilities, enforce security best practices, and integrate with incident response workflows.
- IG3 (Organizational): Targets advanced security needs, including data recovery, security awareness, and penetration testing. CSPM tools can help manage data backup and recovery processes, ensure compliance with organizational policies, and support security testing in cloud environments.
3. ISO/IEC 27001
ISO/IEC 27001 is an internationally recognized standard for information security management systems (ISMS). It provides a systematic approach to managing sensitive company information, ensuring its confidentiality, integrity, and availability. The standard is based on a risk management process and requires organizations to identify information security risks and implement appropriate controls.
- Risk Management: At the heart of ISO/IEC 27001 is a risk management process that involves identifying, analyzing, and addressing security risks. This is highly relevant to CSPM, where cloud environments are continuously assessed for risks such as misconfigurations, unauthorized access, and data breaches.
- Controls: ISO/IEC 27001 includes a comprehensive set of controls, categorized into domains like access control, cryptography, physical security, and incident management. CSPM tools can be configured to monitor these domains continuously, ensuring that cloud resources comply with the relevant controls. For example, CSPM tools can enforce access control policies, monitor for unauthorized access attempts, and ensure that data is encrypted.
4. Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM)
The Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM) is a cybersecurity control framework specifically designed for cloud computing. It provides a detailed set of security controls aligned with industry standards such as ISO/IEC 27001 and NIST. The CCM covers key security domains, including data protection, identity management, and threat detection.
Domains and Controls: The CCM is organized into 16 security domains, each containing specific controls. These domains include:
- Application Security: Ensuring the security of cloud-based applications through secure development practices and regular testing.
- Data Security and Information Lifecycle Management: Protecting data throughout its lifecycle using encryption, access controls, and data loss prevention (DLP) mechanisms.
- Identity and Access Management (IAM): Managing user identities and their access to cloud resources using role-based access control (RBAC), MFA, and privileged access management.
5. Payment Card Industry Data Security Standard (PCI DSS)
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to protect payment card information. It is crucial for any organization that processes, stores or transmits credit card data. The standard includes 12 requirements, covering areas such as network security, access control, and vulnerability management.
Key Requirements:
- Build and Maintain a Secure Network: Requires the implementation of firewalls and secure configurations for systems. CSPM tools can help by monitoring network configurations in the cloud and ensuring compliance with secure baseline configurations.
- Protect Cardholder Data: Mandates the encryption of stored cardholder data and the use of secure transmission methods. CSPM tools can enforce encryption policies across cloud resources and monitor data flows to ensure compliance with PCI DSS.
- Maintain a Vulnerability Management Program: Involves regularly scanning for vulnerabilities and applying patches. CSPM tools automate vulnerability scanning, detect misconfigurations, and help manage patching processes in the cloud.
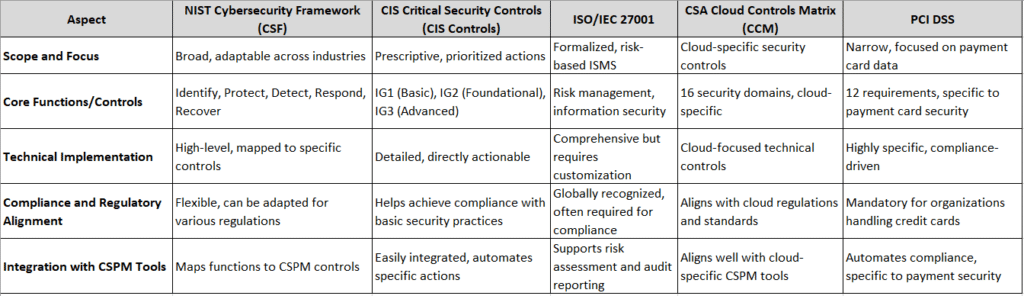
Comparison of Security Frameworks
Understanding the nuances of different security frameworks is essential for selecting the right approach to Cloud Security Posture Management (CSPM). Each framework has unique strengths, focus areas, and levels of detail, making them suitable for different organizational needs and cloud environments. Below is a comparison of the leading security frameworks in terms of scope, applicability, technical controls, and integration with CSPM tools.
Implementation Strategies
Implementing security frameworks within a Cloud Security Posture Management (CSPM) strategy involves a structured approach that ensures alignment with organizational goals, seamless integration with cloud environments, and continuous monitoring for compliance and improvement. Here we take a look at a generalized strategy for implementing any security framework in a CSPM context.
1. Baseline Assessment and Planning
- Conduct a Comprehensive Assessment: Start by thoroughly assessing your cloud environment to identify all assets, existing security controls, vulnerabilities, and compliance requirements. This baseline assessment will help you understand the current security posture and identify gaps that need to be addressed by the chosen security framework.
- Define the Scope: Clearly define the scope of implementation, focusing on the specific cloud resources, services, and data that fall under the framework’s requirements. This helps in tailoring the implementation process to areas of highest risk and regulatory importance.
- Develop an Implementation Plan: Create a detailed implementation plan that outlines the necessary steps, timelines, responsibilities, and resources required. This plan should include prioritizing controls based on risk, regulatory needs, and the criticality of cloud assets.
2. Control Implementation and Integration
- Implement Security Controls: Begin implementing the security controls specified by the framework. Use CSPM tools to automate the deployment and enforcement of these controls across your cloud environment. Controls might include secure configurations, access management, encryption, and continuous monitoring.
- Leverage Automation and CSPM Tools: Integrate CSPM tools to automate the application and monitoring of security controls. For example, CSPM tools can enforce secure configurations, detect and respond to threats in real-time, and ensure continuous compliance with the framework’s requirements.
- Establish Continuous Monitoring: Set up continuous monitoring to ensure that the implemented controls remain effective over time. CSPM tools should be configured to provide real-time alerts, track changes in cloud resources, and automatically remediate misconfigurations or violations of security policies.
3. Compliance and Reporting
- Regular Audits and Assessments: Conduct regular internal audits and assessments to evaluate the effectiveness of the implemented controls. Use CSPM tools to generate audit reports that demonstrate compliance with the security framework and identify areas for improvement.
- Continuous Compliance Monitoring: Ensure continuous compliance with the framework by using CSPM tools to monitor cloud environments in real time. These tools should provide visibility into compliance status, highlight deviations, and facilitate corrective actions.
- Documentation and Reporting: Maintain comprehensive documentation of the implementation process, controls applied, and compliance status. Regularly generate and review reports from CSPM tools to ensure that your cloud security posture remains aligned with the security framework.
4. Continuous Improvement and Adaptation
- Review and Update Controls: Regularly review the effectiveness of the implemented controls and make necessary updates based on new threats, changes in cloud infrastructure, or evolving regulatory requirements. CSPM tools can provide insights into areas where controls may need to be strengthened or adjusted.
- Adapt to New Cloud Services: As your cloud environment evolves and new services or technologies are adopted, ensure that your security framework implementation adapts accordingly. CSPM tools should be updated to cover new resources and maintain continuous protection.
- Foster a Culture of Security: Promote a culture of security within your organization by educating teams about the importance of cloud security and the role of the chosen framework. Regular training and awareness programs can help maintain a strong security posture.
K8s Security – The Ultimate Guide
Dive deep into the ever evolving landscape of Kubernetes security, explore best practices, and discover potential pitfalls.
Learn More
Future Trends
The future of Cloud Security Posture Management (CSPM) will be shaped by emerging technologies, evolving threats, and regulatory changes. Here are the key trends expected to influence CSPM and security frameworks.
1. AI and Machine Learning Integration
AI and ML will become crucial in enhancing CSPM tools for predictive analytics, automated threat detection, and adaptive security controls.
- Predictive Analytics: AI will forecast potential threats, enabling proactive measures.
- Automated Detection: ML algorithms will improve real-time threat detection and response.
- Adaptive Controls: Security controls will dynamically adjust to evolving risks.
2. Expansion of Zero Trust Architectures
The adoption of Zero Trust models will grow, emphasizing continuous verification and microsegmentation in cloud environments.
- Microsegmentation: CSPM tools will enforce network segmentation to limit lateral movement.
- Continuous Verification: Ongoing authentication and authorization will be essential.
- Dynamic Policies: Access controls will adapt based on real-time context.
3. Focus on Multi-Cloud Security
As multi-cloud strategies expand, CSPM tools will need to offer unified security management across diverse cloud platforms.
- Unified Management: CSPM tools will provide consistent security across all cloud providers.
- Interoperability: Seamless integration with cloud-native services will be crucial.
- Cross-Cloud Visibility: Enhanced visibility and monitoring across multi-cloud environments will be a priority.
4. Automated Compliance
Increasing regulatory demands will drive the automation of compliance checks and reporting.
- Automated Audits: CSPM tools will automate compliance assessments and reporting.
- Real-Time Dashboards: Continuous compliance monitoring will provide up-to-date insights.
- Regulatory Updates: CSPM tools will automatically adjust to new regulations.
5. Evolution into CNAPPs
CSPM tools will evolve into Cloud Native Application Protection Platforms (CNAPPs), integrating security across cloud-native applications.
- Integrated Functions: CNAPPs will combine CSPM with workload protection and entitlement management.
- Contextual Insights: Correlating data across layers for accurate threat detection.
- Developer Tools: CNAPPs will support secure application development from the beginning.
Conclusion
As organizations increasingly rely on cloud environments, the importance of robust security frameworks and Cloud Security Posture Management (CSPM) cannot be overstated. Implementing leading security frameworks through CSPM tools provides a structured approach to safeguarding cloud resources, ensuring compliance, and mitigating evolving threats.
By leveraging automation, continuous monitoring, and real-time compliance checks, organizations can maintain a strong security posture in the face of dynamic cloud challenges.
The future of CSPM will be shaped by trends such as AI integration, Zero Trust adoption, and the evolution of CSPM into comprehensive Cloud Native Application Protection Platforms (CNAPPs). Staying ahead of these trends will be key to maintaining resilient, secure, and compliant cloud operations.
Read more about ARMO’s CSPM solution here.

Unifying AppSec, CloudSec and DevSec
The only runtime-driven, open-source first, cloud security platform:
Continuously minimizes cloud attack surface
Secures your registries, clusters and images
Protects your on-prem and cloud workloads