MongoBleed (CVE-2025-14847): Unauthenticated Memory Disclosure in MongoDB
A newly disclosed MongoDB vulnerability, tracked as CVE-2025-14847 and informally referred to as MongoBleed, allows...

Sep 28, 2024
A series of critical vulnerabilities has been uncovered in the Common Unix Printing System (CUPS), specifically in the cups-browsed component and related libraries. This vulnerability chain allows remote, unauthenticated attackers to potentially execute arbitrary code with root privileges on affected systems. The discovery highlights significant security risks in a widely-used open-source component and raises crucial questions about legacy system support and security in modern IT environments.
Common UNIX Printing System (CUPS) is an open source printing system that allows a system to act as a print server. It manages print jobs and queues and provides support for printing via the Internet Printing Protocol (IPP), making it a widely used printing service on UNIX-like operating systems, including Linux and macOS
On September 26 Simone Margaritelli, a security researcher, published a blog post that sums up the vulnerabilities. According to Margaritelli, a remote unauthenticated attacker can exploit vulnerabilities in printer systems to replace or install new IPP (Internet Printing Protocol) URLs. This allows the attacker to execute arbitrary commands on the target computer when a print job is initiated, without the user’s knowledge. Margaritelli noted that there are some conditions for this vulnerability to be exploited.
It’s important to note that while this vulnerability chain is severe for affected systems, its impact may be limited in modern containerized and cloud-native environments. Most container images, especially those built on minimal base images or following security best practices, typically do not include the CUPS printing system or the vulnerable CUPS-browsed service. Similarly, many cloud-native applications and microservices architectures don’t rely on traditional printing services. This means that a significant portion of modern, containerized workloads are likely not directly affected by this vulnerability chain. However, CISOs and security teams should still conduct thorough assessments, as legacy applications, development environments, or specific use-cases might still incorporate CUPS, potentially introducing risk into otherwise secure container ecosystems.
In light of vulnerabilities like the CUPS exploit chain, ARMO Platform offers critical advantages for Cloud and Kubernetes environments. Our Vulnerability “in use” feature alerts on vulnerabilities which are in components actually loaded into memory, filtering out issues in dormant CUPS libraries. This approach allows security teams to prioritize real, active threats efficiently. Furthermore, ARMO Platform’s threat detection and response provide an additional layer of defense. By continuously monitoring for anomalies such as unexpected process launches or unusual network activity, ARMO identifies potential exploitation attempts of vulnerabilities like those in CUPS, even in scenarios where the vulnerable component unexpectedly exists in the environment. This multi-faceted approach – combining smart vulnerability filtering with advanced behavioral analysis – ensures that organizations can maintain a robust security posture against both known vulnerabilities and novel attack vectors in their Kubernetes ecosystems.
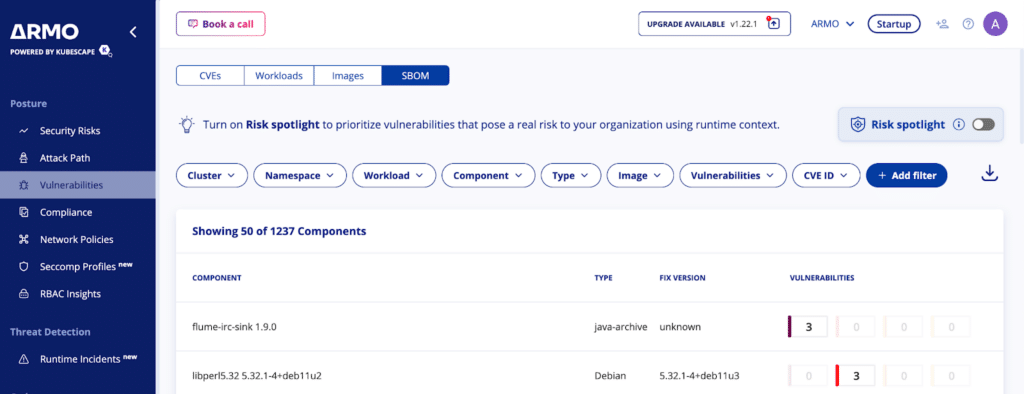
Using the ARMO’s SBOM view one can search for the CUPS component to see if it even exists in the environment.
A newly disclosed MongoDB vulnerability, tracked as CVE-2025-14847 and informally referred to as MongoBleed, allows...

Within 24 hours, three new high-severity vulnerabilities were disclosed in runc, the low-level runtime that...

Hi there,We’ve just dropped a fresh batch of updates to help you cut through the...