The 3 Biggest Cloud Workload Threats (and Why Teams Miss Them)
Introduction — Moving to the Cloud Changed Everything (Even If the Cloud Didn’t) In this...

Feb 13, 2025
Unlike static environments, cloud workloads are constantly shifting, with containers and virtual machines spinning up and down, and crucial sensitive information flowing dynamically across multiple platforms. Recent incidents, such as the increase in container-based malware infections and cloud misconfigurations resulting in major data breaches, have highlighted the need for runtime security.
The 2023 MOVEit file transfer software vulnerability, for instance, saw threat actors exploiting zero-day flaws to inject malware into active cloud environments, disrupting critical infrastructure worldwide. Similarly, cryptojacking attacks such as the TeamTNT campaign have been increasingly targeting cloud environments, utilizing runtime resources for illicit mining activities while remaining under the radar of traditional defenses. These events demonstrate the growing sophistication of threats targeting the cloud, where securing workloads at runtime has become non-negotiable.
Runtime security is now indispensable as organizations shift towards more distributed and ephemeral infrastructures. It addresses a critical gap in safeguarding cloud workloads by actively monitoring, detecting, and responding to real-time threats. This article will explore why runtime security is essential in cloud environments, shedding light on its key components and the challenges that must be addressed to ensure comprehensive protection in the cloud.
Cloud Detection and Response (CDR) is a complementary approach to “shift-left” security that is often subscribed to in cloud-native environments. This approach seeks to protect applications, containers, and workloads actively running in cloud environments. Traditional security measures often focus on protecting the perimeter or ensuring compliance before deployment. CDR operates within production environments, continuously monitoring processes, configurations, and behaviors as they execute. Its primary purpose is to detect and mitigate security threats in real time, ensuring that workloads remain secure even in runtime.
Traditional security measures typically revolve around preventative measures such as firewall configurations, network security, and vulnerability scanning conducted before an application goes live. While these are important, they are often static and fail to account for the fluid nature of cloud workloads that constantly scale, evolve, and shift across environments. CDR differs by focusing on live monitoring and active threat detection at the time when organizations are most vulnerable—during workload execution.
With traditional security approaches, threat detection often relies on log sources and baselines, however with the dynamic nature of containers and cloud-native workloads, these resources spin up and down as the load changes. This way traditional security control and detection mechanisms are rendered ineffective since these workloads often cannot be tied down to a specific log source or baseline.
In cloud environments, workloads are often ephemeral and scalable, with containers and virtual machines spinning up or down based on demand. This elasticity, combined with the complexity of distributed systems and multi-cloud environments, creates an ever-changing attack surface.
CDR is crucial in this context because threats can emerge after deployment. This is particularly true as workloads interact with external systems or encounter evolving threat vectors such as zero-day vulnerabilities, misconfigurations, or malicious intruders or insiders. CDR ensures that security controls adapt and respond to protect workloads in real-time, even in these fluid and dynamic cloud environments. This helps minimize the risk of exploitation while still allowing users to enjoy the full benefits of the cloud environments.
Several components of CDR ensure that threats are detected in time. Here, we will focus on some key components:
Real-time observation of applications, containers, and workloads as they operate, ensures that any suspicious behavior is detected instantly. By constantly monitoring the environment, CDR can quickly identify and respond to threats as they emerge. Threat detection mechanisms work together with continuous monitoring to analyze system activity, log data, and network traffic, identifying potential security incidents in real-time.
Behavioral analysis focuses on understanding and establishing normal activity patterns within an environment. Monitoring behaviors such as network communication, system calls, and user activity, can detect subtle anomalies that might indicate malicious activity. This proactive approach helps uncover sophisticated threats that may bypass traditional security defenses, which only rely on known threat signatures.
Anomaly detection builds on the foundation of behavioral analysis, using machine learning algorithms and statistical models to identify unusual activities that deviate from established norms. Anomalies could be signs of previously unknown threats, such as zero-day exploits, that might not have a known signature or pattern. By detecting these outliers, anomaly detection can uncover potential attacks early, before they cause significant harm.
Automated response mechanisms enable CDR to react swiftly to identified threats without waiting for human intervention. When a threat is detected, actions such as isolating a compromised container, terminating suspicious processes, or triggering alerts can be initiated automatically. Automated remediation not only reduces the time it takes to respond to security incidents but also helps limit the scope of an attack, minimizing its blast radius. This capability is particularly important in cloud environments, where workloads are dynamic and fast-moving.
Container escapes occur when an attacker breaks out of the isolated environment of a container and gains access to the host system or other containers. This breach can lead to lateral movement within the cloud infrastructure, exposing other services and data to attack. For example, a 2023 Kubernetes vulnerability (CVE-2023-3676) exploited a flaw in which a malicious container could bypass security controls and gain root access to the underlying host system. This type of vulnerability emphasizes the importance of runtime security in preventing unauthorized access and limiting the damage caused by container escape attacks.
Cloud environments are often targeted by attackers seeking to gain unauthorized access through stolen credentials.
A prominent example is the August 2022 social engineering attack on Twilio, where attackers gained access to Twilio’s internal systems by tricking employees into divulging their credentials. Once inside, the attackers were able to access customer data and launch further phishing attacks. This incident illustrates the critical importance of securing credentials and implementing robust authentication mechanisms to prevent unauthorized access.
Misconfigurations in cloud settings are a common yet critical security concern. Misconfigurations can lead to unintentional data exposure or unauthorized access if security policies are not properly enforced and reviewed regularly.
A well-known example is the 2018 case in which an unauthorized actor gained access to Tesla’s Kubernetes console. allowing them to run cryptojacking containers to mine cryptocurrency using Tesla’s cloud resources. From there, the attackers both abused Tesla’s cloud resources for cryptojacking and accessed private data held in Amazon’s S3 service.
Malware and cryptojacking increasingly target cloud resources, leveraging the scale and processing power of cloud environments for malicious purposes. Cryptojacking involves using cloud instances to mine cryptocurrencies without user consent, depleting resources and increasing operational costs. This type of attack can also serve as a foothold for further malicious activities.
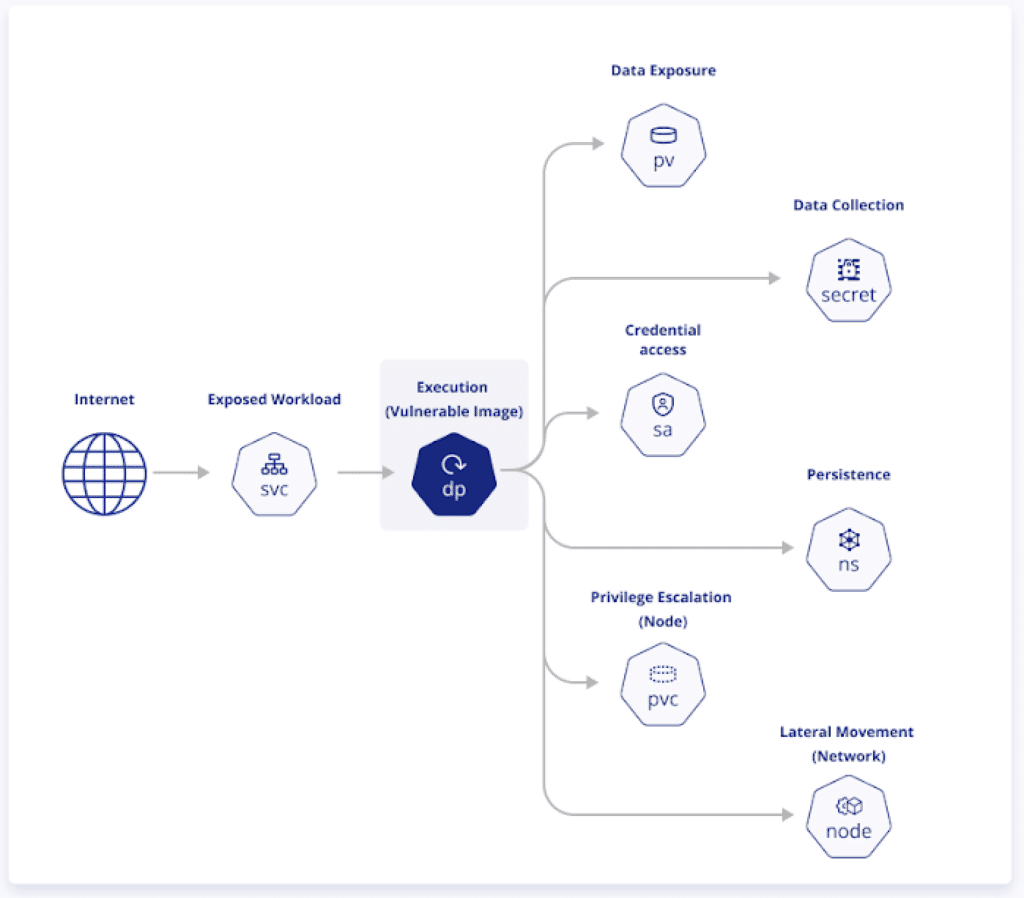
Securing cloud environments presents unique challenges due to their dynamic, scalable nature. As organizations increasingly rely on cloud services, addressing these runtime security challenges becomes crucial. Here are some of the key issues:
Cloud environments often involve ephemeral workloads that are short-lived and dynamically created. This transient nature can make it difficult to apply consistent security measures. Traditional security tools designed for static environments may not effectively handle the rapid creation and termination of cloud resources. Implementing runtime security solutions that can adapt to these changing workloads is essential to ensure ongoing protection.
Many organizations use multiple cloud providers to avoid vendor lock-in or leverage specific services. Managing security across different cloud platforms can be complex, as each provider has its own set of security tools, policies, and configurations. Ensuring consistent security practices and monitoring across multiple cloud environments requires a unified approach and integration of various security solutions to provide comprehensive protection.
Cloud environments are designed for scalability and performance, which sometimes conflicts with security measures. Implementing extensive security controls can impact system performance, leading to slower response times and reduced efficiency. Organizations must strike a balance between robust security measures and maintaining optimal performance, ensuring that security practices do not unduly hinder operational efficiency.
Compliance with regulatory requirements and industry standards is a significant challenge in cloud environments. Different regulations may apply based on geographic location, industry, or the type of data being handled. Ensuring that cloud environments meet these compliance requirements while maintaining security can be complex, particularly when dealing with diverse data protection laws and standards. Organizations need to implement comprehensive compliance monitoring and reporting mechanisms to address these requirements effectively.
Cloud detection and response is a critical component of modern cybersecurity strategies, given the dynamic and scalable nature of cloud computing. As cloud infrastructures become more integral to business operations, they also present a broader and more complex attack surface. Understanding and addressing the key threats—such as container escapes, unauthorized access, malware and cryptojacking, and misconfiguration exploits—is essential for maintaining robust security.
The challenges associated with cloud runtime security include managing ephemeral workloads, navigating multi-cloud environments, balancing security with performance, and ensuring compliance, which requires a proactive and adaptive approach. Implementing continuous monitoring, integrating advanced security tools, and maintaining a comprehensive compliance framework are crucial steps in safeguarding cloud environments.
Organizations must prioritize CDR to protect their dynamic cloud workloads from emerging threats and vulnerabilities. By adopting a holistic security strategy that addresses these challenges, businesses can enhance their resilience against attacks and secure their cloud environments effectively.

Introduction — Moving to the Cloud Changed Everything (Even If the Cloud Didn’t) In this...

If you are dealing with securing cloud infrastructure, containers and applications, you probably have several...

Within 24 hours, three new high-severity vulnerabilities were disclosed in runc, the low-level runtime that...