Enhancing Application Security with Container Runtime Security
Understanding Containerization and Container Runtime Containerization, a form of lightweight virtualization, lets applications inhabit their...
Apr 15, 2025
“Anomaly detection” has become a core capability in modern cloud security. Yet despite its ubiquity in product marketing and platform docs, one basic question remains surprisingly unsettled: What exactly is an anomaly?
The answer depends on who you ask – and how they approach threat detection.
Broadly speaking, there are two prevailing schools of thought in defining what constitutes an anomaly:
From this viewpoint, an anomaly is any deviation from established norms that are defined and documented – often in the form of known attack chains, compliance requirements, or behavioral policies. These are encoded into rules or signatures:
Rules-based detection is grounded in experience, research, and real-world incident data. It’s methodical, explainable, and often tightly aligned with compliance needs.
This school takes a more adaptive approach. Here, an anomaly is any behavior that meaningfully deviates from what the system normally does, regardless of whether it’s been seen before or fits a known pattern.
This model is designed to detect the unknown:
In traditional, relatively static IT environments, rules-based approaches worked well. You could define what was allowed, build a library of threat indicators, and enforce them reliably.
But cloud-native environments – especially those built with Kubernetes, containers, and microservices – don’t play by the same rules.
In short, there are many, many workloads out there, and they all behave differently. In addition, they are always changing. This new reality makes it nearly impossible to predefine every legitimate behavior – or every possible malicious one. Creating and maintaining rules to cover the well-known is hard enough, writing rules to cover the unknown is impossible.
Rules-based systems bring another challenge: operational complexity.
Maintaining thousands of rules is:
False positives become a major problem, and threat detection starts to feel like a constant game of tuning alerts and silencing noise.
This is where behavioral-based anomaly detection shines.
Rather than trying to predict and predefine everything, it observes what’s normal, builds a model (like ARMO’s Application Profile DNA), and flags anything that deviates from that baseline.
None of these require prewritten rules to detect. The behavior itself is the signal.
Neither approach is sufficient alone.
That’s why ARMO combines both. But increasingly, as cloud environments grow more dynamic and attackers grow more sophisticated, behavioral anomaly detection is becoming the first line of defense.
It catches what rules can’t predict.
So, what is an anomaly?
Maybe it’s time we moved past trying to define it in rigid terms.
Instead, we should think about it more like this:
An anomaly is any behavior that doesn’t belong – whether we’ve seen it before or not.
In a world of zero-days, supply chain attacks, and cloud complexity, the unknown is the new normal
And anomaly detection needs to evolve accordingly.
Try ARMO CADR and see what Behavioral-based anomaly detection can do for you.

Understanding Containerization and Container Runtime Containerization, a form of lightweight virtualization, lets applications inhabit their...
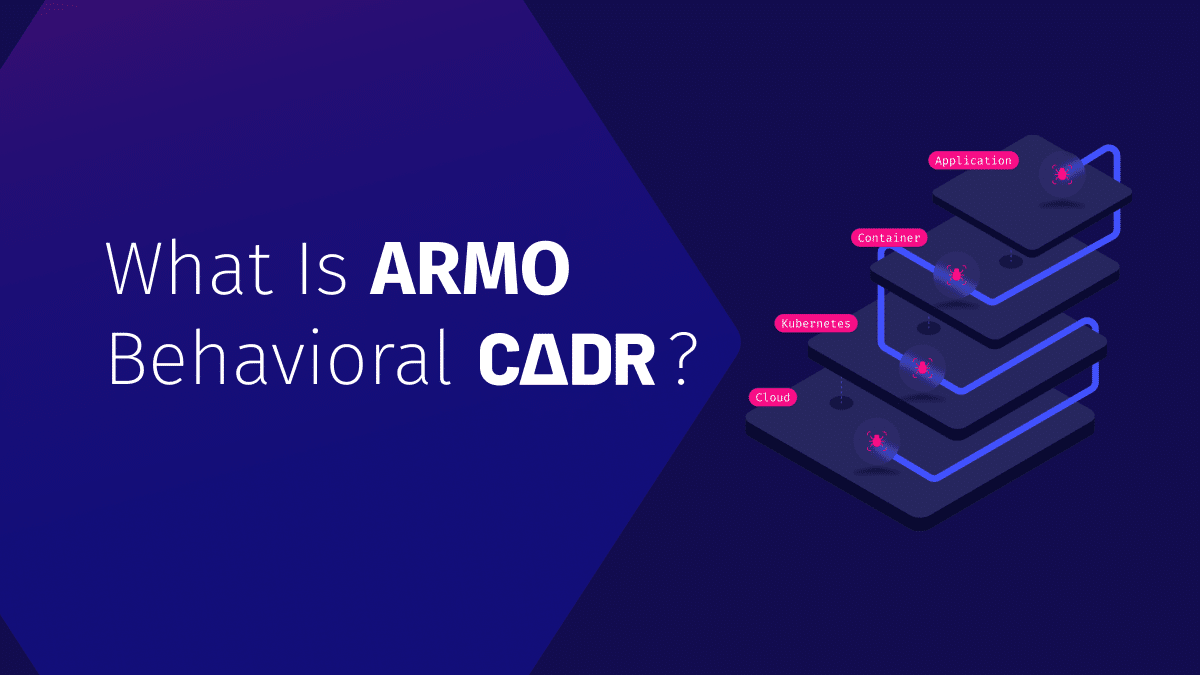
As organizations increasingly adopt cloud-native architectures, they face a sprawling attack surface with novel threats...
Introduction CVE-2025-1094 presents a critical challenge to established SQL security paradigms, effectively circumventing fundamental best...