Beyond the noise: runtime-based vulnerability management for effective threat control
Introduction In an ideal world, patching every vulnerability before attackers discover them would be a...

Introduction In an ideal world, patching every vulnerability before attackers discover them would be a...

In the era of cloud computing, Kubernetes has emerged as a true cornerstone of cloud-native...

Introduction This is not a beginner’s blog post. As such, we will not tell you...
Kubernetes 1.29 will be the last release from the Kubernetes team for 2023. The new...

In the rapidly evolving world of container orchestration, developers have come to rely on Kubernetes...

Addressing Common Vulnerabilities and Exposures, known as CVE patching, is a practice of applying updates...

Guest post originally published on Kubescape’s blog by Oshrat Nir, Developer Advocate at ARMO and a Kubescape contributer. Introduction: Vulnerability Exploitability eXchange...
GitOps can be a powerful means of achieving continuous compliance in Kubernetes deployments. It provides...

While Kubernetes adoption continues to soar, it has become a prime target for cyberattacks. Unfortunately,...
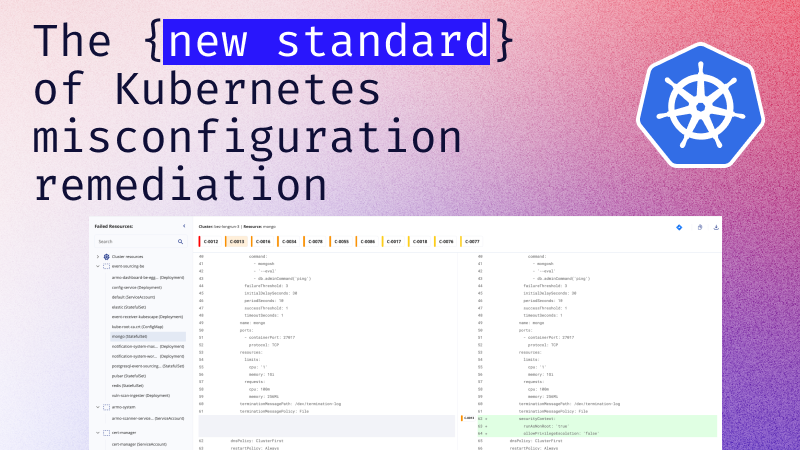
According to research done by ARMO, 100% of Kubernetes clusters that were tested contained at...
In this post we’re going to unpack some of Red Hat State of Kubernetes security...
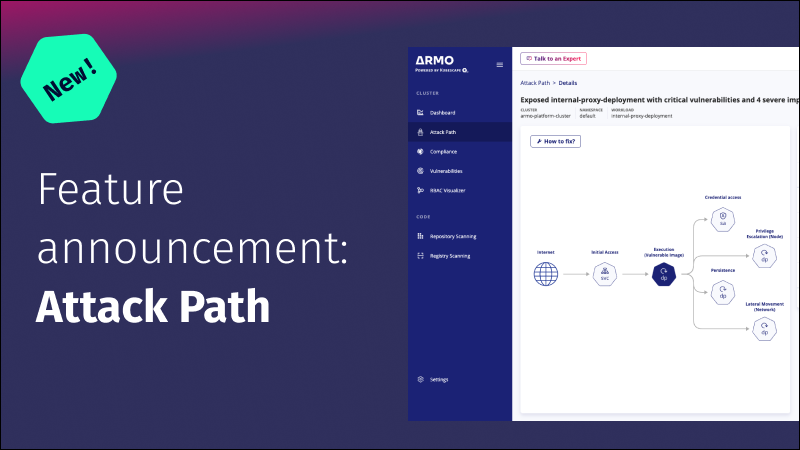
Discover the importance of mapping attack paths in Kubernetes and learn how to effectively enhance...