ARMO named in Gartner® Cool Vendors™ report
We are excited and honored to announce that we were selected as Gartner Cool Vendor...
 Blog
Blog
Oct 24, 2023
In today’s world of limited time, we need to be laser-focused on our priorities. This goes double for mission-critical activities, like cybersecurity. We want to prioritize fixing the issues that have the most significant impact on our security posture.
An attack path is like a roadmap for attackers, outlining the steps they can take to exploit security weaknesses. They start from an initial entry point and navigate through vulnerabilities and misconfigurations to reach valuable assets, aiming to steal data or cause harm.
The importance of mapping attack paths is that it allows you to concentrate on the activities that generate the most value for your cyber security defense.
In an environment like Kubernetes that is constantly changing and can include thousands of different weaknesses (misconfigurations, vulnerabilities and access control), the question as to which step and weakness to concentrate on, becomes even more pressing.
With the release of the new attack path feature, ARMO is enabling Kubernetes users to easily find the answer. It enables teams to prioritize work and offers ways to fix security issues based on their real impact. Issues are addressed in context, instead of in isolation. Thus, making your security investment much more effective.
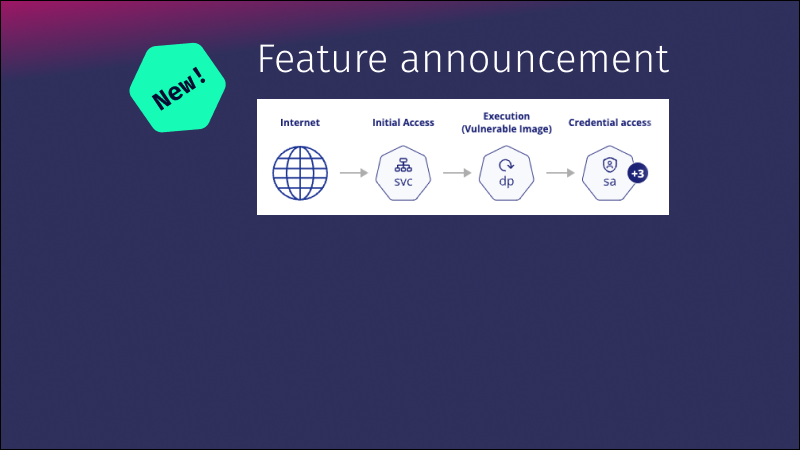
An attack path is a visual representation of the specific sequence of steps an attacker can take to exploit vulnerabilities or misconfigurations and gain unauthorized access to a system. This can potentially result in the compromise of sensitive data or system disruption. In the next section, we’ll explore two types of attack paths based on the MITRE ATT&CK Matrix.

This type of attack path refers to a workload that is accessible through a service or ingress point. When such a workload contains critical vulnerabilities and misconfigurations, it is vulnerable to exploitation by malicious actors.
Exploiting the weaknesses detailed in this type of attack path could lead to significant consequences. These include unauthorized data access and control over other Kubernetes components. You can block this type of attack path by fortifying a single step in the path. Thus, protecting yourself from potential exploitation.
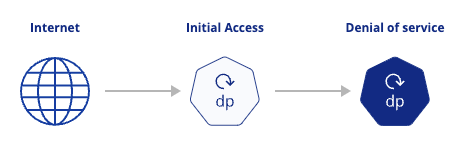
Similar to the previous type, this type of attack path refers to a workload that is accessible through a service or ingress point. However, in this case the crucial problem is missing resource (CPU and/or memory) limits definitions.
Exploiting the weaknesses detailed in this type of attack path could result in a denial of service scenario, impacting system performance and stability. You can block this type of attack path by fortifying a single step in the path. Thus, protecting yourself from potential exploitation.
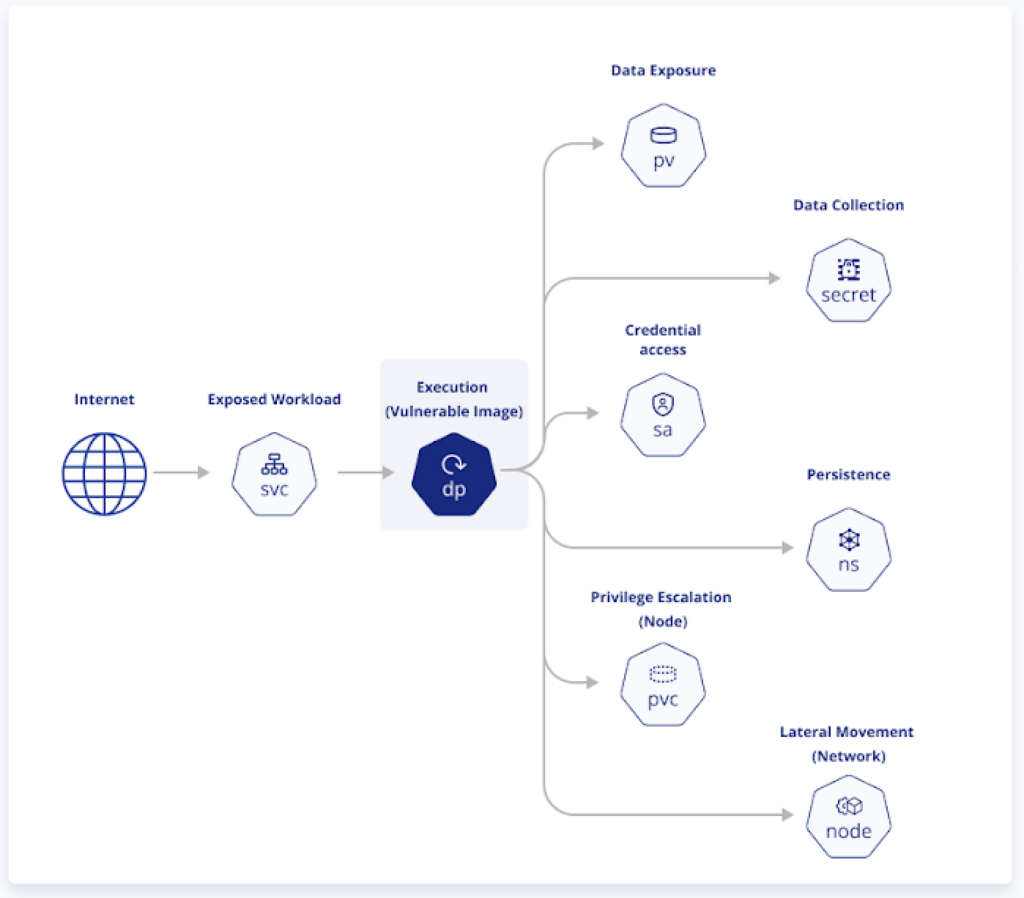
As we mentioned the graph highlights weak spots in your Kubernetes infrastructure and details how attackers could exploit them. It displays misconfigurations and vulnerabilities inviting an attack. Each step the attacker can take is represented as a node in the graph, with each node containing one or more specific misconfigurations or vulnerabilities.
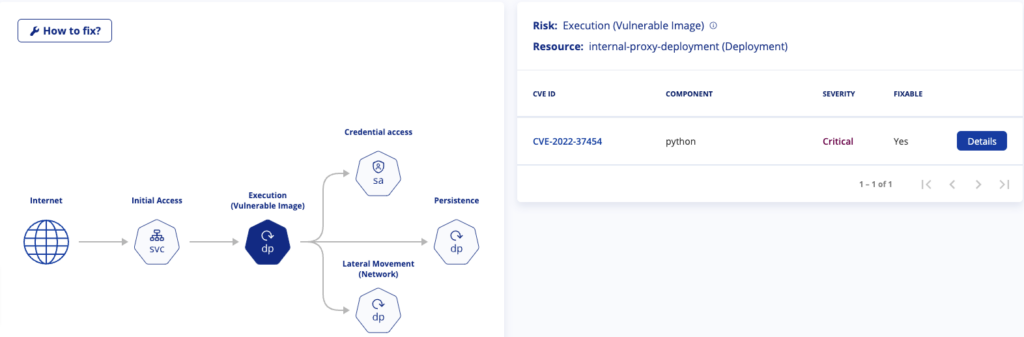
To block an attack path, select a step and resolve all the security issues associated with it. These issues could be misconfigurations or vulnerabilities.
An attack path consists of several steps. To block a path, you need to disable at least one of its steps. Each step can be fixed by addressing all its related security issues. For instance, to block the attack path on top, one could focus on the “Execution” step. By resolving its associated security issue, CVE-2022-37454, this attack path will be blocked.
Visit our docs to read how to use the attack path using ARMO platform.
In the ever-evolving landscape of cybersecurity, understanding the ‘Attack Path’ is your secret weapon. Visualize the journey of potential attackers, prioritize vulnerabilities and misconfigurations based on real-world impact, and fortify your Kubernetes environment. By focusing on a single step, you can block these attack paths, ensuring that threats are not just managed but neutralized. Leverage Attack Paths and transform your security approach from hit or miss, to always be on point. Stay one step ahead of malicious actors, always.

The only runtime-driven, open-source first, cloud security platform:
Continuously minimizes cloud attack surface
Secures your registries, clusters and images
Protects your on-prem and cloud workloads

We are excited and honored to announce that we were selected as Gartner Cool Vendor...

Learn about Kubernetes compliance challenges, consequences of non-compliance, and get guidance on maintaining a secure...
As organizations increasingly adopt cloud-native architectures, they face a sprawling attack surface with novel threats...