Kubernetes RBAC: Deep Dive into Security and Best Practices
This guide explores the challenges of RBAC implementation, best practices for managing RBAC in Kubernetes,...
 Blog
Blog

Dec 29, 2024
Role-Based Access Control (RBAC) is important for managing permissions in Kubernetes environments, ensuring that users have the appropriate level of access to resources.
However, organizations often encounter challenges in effectively managing their role-based access control systems, which can lead to security vulnerabilities and compliance issues. Below are the best RBAC tool options for managing Kubernetes RBAC, ensuring compliance and enhancing security within cloud-native applications.
RBAC is a foundational element in Kubernetes that supports security, resource management, and compliance:
Despite its importance, managing RBAC in Kubernetes presents several challenges that organizations must navigate:
These challenges highlight the need for practical tools to streamline RBAC management.
| Tool Name | Key Features | Advantages | Key Takeaways |
|---|---|---|---|
| ARMO Platform | Visual RBAC mapping, deep configuration analysis, integration with KSPM, focus on least privilege. | Identifies over-privileged users, ensures compliance, integrates with DevOps workflows. | Enhances visualization and management of RBAC configurations for secure clusters. |
| Fairwinds RBAC Tools |
|
Simplifies large-scale RBAC management, integrates with CI/CD workflows, supports audits. | Streamlines RBAC management and audits with complementary tools. |
| CyberArk KubiScan | Scans clusters for risky permissions, token extraction, identifies subjects with sensitive access. | Highlights security vulnerabilities, identifies excessive privileges, supports secret data security assessments. | Offers detailed risk assessment for secure Kubernetes environments. |
| Rapid7 RBAC Tool | Graphical RBAC representations, permission analysis, policy generation and querying, integrates with `kubectl`. | Ensures adherence to least privilege, reduces wildcard permissions, simplifies complex RBAC configurations. | Robust visualization and analysis for secure RBAC policies. |
| Palo Alto RBAC-Police | Permission analysis for various identities, Rego-based policy evaluations, library of 20+ policies. | Customizable policies, identifies misconfigurations, supports namespace-specific assessments. | Enhances security with a policy-driven approach and tailored evaluations. |
| Krane | Static analysis, custom risk rules, CI/CD pipeline integration, machine-readable reports. | Comprehensive dashboard, ad-hoc querying with CypherQL, highlights RBAC risks systematically. | Combines visualization and alerting to mitigate RBAC misconfigurations. |
| kubectl-bindrole | CLI for mapping Roles and RoleBindings to specific identities. | Saves time in audits, customizable output formats for easy integration with other tools. | Efficiently identifies roles linked to identities to enforce least privilege. |
| kubectl-who-can | Queries RBAC permissions for specific actions/resources. | Detailed insights into subjects’ privileges, supports compliance and security audits. | Accessible and easy-to-use plugin for auditing RBAC permissions. |
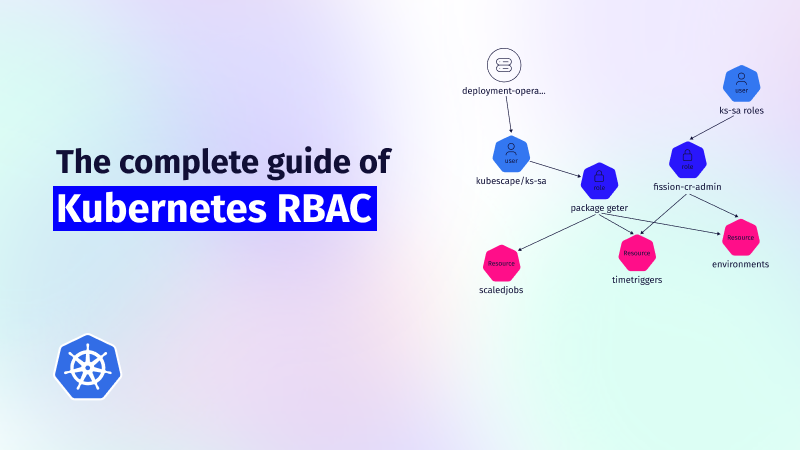
ARMO Platform offers a robust Kubernetes RBAC visualization tool designed to help administrators understand different roles and capabilities at a birds-eye view. This role-based access control tool enables comprehensive visualization and analysis of RBAC configurations, ensuring adherence to the principle of least privilege. The platform streamlines the management of access levels across an environment by emphasizing user permissions.
ARMO Platform’s RBAC solutions empower Kubernetes administrators to manage and visualize access controls, reducing the risk of over-privileged access and enhancing overall cluster security. Building upon an open-source foundation, ARMO enables integrations of these tools into DevOps workflows and adds efficiency to Kubernetes RBAC management.
FairwindsOps offers two Kubernetes RBAC tools: `rbac-manager` and `rbac-lookup`. `rbac-manager` is a Kubernetes operator that simplifies the management of Role Bindings and Service Accounts through declarative configurations. `rbac-lookup` is a command-line interface (CLI) tool that enables users to easily find roles and cluster roles attached to any user, service account, or group name within a Kubernetes cluster.
FairwindsOps’ rbac-manager and rbac-lookup tools offer complementary solutions for managing and auditing Kubernetes RBAC configurations. Together, they streamline RBAC management and auditing processes, contributing to more secure and efficient Kubernetes operations.
KubiScan is an open-source tool developed by CyberArk to scan Kubernetes clusters for risky permissions. It assists administrators in identifying permissions that attackers could exploit to compromise clusters, saving time and offering insights into user permissions and access risks.
KubiScan is a valuable tool for identifying and mitigating risky permissions. Its comprehensive scanning capabilities, including token extraction, subject analysis, and CVE scanning, provide a robust approach to securing Kubernetes environments. KubiScan supports a secure and compliant Kubernetes infrastructure by integrating with major cloud services and providing detailed risk assessments.
`rbac-tool` is a free utility developed by Alcide, now part of Rapid7, designed to simplify the management and analysis of RBAC configurations. It offers a suite of commands to visualize, analyze, generate, and query policies, enhancing security and operational efficiency within Kubernetes clusters.
`rbac-tool` enhances cluster security by ensuring RBAC configurations adhere to best practices. Its visualization, analysis, generation, and querying capabilities offer a robust approach to managing RBAC policies. This integration with `kubectl` and support for installation via `krew` facilitates seamless access and usability within Kubernetes environments.
`rbac-police` is an open-source tool developed by Palo Alto Networks to assess and manage permissions within Kubernetes clusters. It retrieves RBAC permissions associated with Kubernetes identities, including service accounts, pods, nodes, users, and groups. It evaluates permissions using policies written in Rego. This RBAC software helps administrators identify privileges associated with different identities and ensures compliance with mandatory access controls.
`rbac-police` aims to enhance cluster security by ensuring RBAC configurations adhere to the principle of least privilege. Its policy-driven approach, combined with the flexibility of Rego, allows for tailored evaluations to identify and mitigate potential security risks associated with authorization configurations.
Krane is an open-source RBAC tool developed by Appvia that performs static analysis and visualization of Kubernetes RBAC configurations. It identifies potential security risks in RBAC design and offers suggestions for mitigation, ensuring it aligns with best practices.
Krane is a comprehensive RBAC solution that enhances cluster security by ensuring configurations adhere to best practices. Its combination of static analysis, visualization, and alerting capabilities provides a robust solution for managing RBAC risks.
`kubectl-bindrole` is a command-line tool found on Github designed to identify Kubernetes Roles and RoleBindings associated with a specific ServiceAccount, Group, or User. It saves administrators time in auditing and managing RBAC configurations by pinpointing which roles are granted to particular identities.
`kubectl-bindrole` is a reasonable option for those seeking to understand and manage RBAC configurations. Identifying associations for specific identities enables alignment within the principle of least privilege, which ultimately enhances cluster security.
`kubectl-who-can` is an open-source Kubernetes plugin developed by Aqua Security. It enables users to determine which subjects (such as users, groups, or service accounts) have specific RBAC permissions to perform actions on various resources within a Kubernetes cluster, improving security and compliance.
`kubectl-who-can` enhances cluster security by ensuring RBAC configurations adhere to best practices. Its integration with `kubectl` and support for various installation methods make it accessible and easy to use. Identifying the privileges associated with each subject is essential for maintaining a secure and compliant Kubernetes environment.
This article reviewed the top tools for managing Kubernetes RBAC, showcasing their unique features and benefits. It underscores the importance of choosing the right RBAC solutions to strengthen security and maintain compliance in Kubernetes environments.
Organizations are encouraged to evaluate their role-based access control definitions and consider adopting these tools to improve management and oversight in their Kubernetes environment, ultimately leading to a more secure and compliant infrastructure. With ARMO Platform’s RBAC Visualizer, administrators can easily identify and manage privileges assigned to users, service accounts, and groups across your Kubernetes clusters. Simplify the process of enforcing the principle of least privilege, enhance security, and ensure compliance, all in one intuitive platform. Try the ARMO Platform today for free and take your RBAC management to the next level.

The only runtime-driven, open-source first, cloud security platform:
Continuously minimizes cloud attack surface
Secures your registries, clusters and images
Protects your on-prem and cloud workloads
This guide explores the challenges of RBAC implementation, best practices for managing RBAC in Kubernetes,...

In the dynamic world of Kubernetes, container orchestration is just the tip of the iceberg....

Kubernetes is a container orchestration tool that helps with the deployment and management of containers....