ARMO CADR Uncovers Multiple Crypto Miner Attack Operations
Introduction: Luring in the Threat Actors The best way to understand real-world attacks is to...

Feb 7, 2023
We are happy to announce that ARMO Platform users can now utilize ChatGPT to quickly and easily create custom controls. ARMO is the first Kubernetes security company to offer this kind of integration. Read all about it 👇
Security researchers and DevSecOps professionals codify security & compliance best practices in controls. These are preventative, detective, or corrective measures that can be taken to avoid or contain, a security breach.
One of the most important steps you can take to secure and harden your Kubernetes clusters and CI/CD pipeline is to use security policies based on controls. They scan for errors in configuration files (e.g. YAML files, Helm charts, etc), Git code repositories, workloads, worker nodes, container images, API servers and more.
ARMO Platform, based on Kubescape, comes with hundreds of controls out-of-the-box. They can be used in either industry recognized benchmarks and guidelines (CIS, NSA, MITRE, etc.) or custom frameworks (a framework that a user can create by choosing specific controls to meet his/her specific needs and requirements). These controls test a specific aspect of the CI/CD and Kubernetes Security posture.
One of the most popular tools to create these controls and run them is Open Policy Agent (OPA). OPA uses an open-source language owned by the Linux foundation called Rego. Like many things in the world of cloud-native, there is a skill gap when it comes to usage of Rego, as well as a learning curve to gain proficiency in it.
OPA and Rego are, respectively, the tool and language of choice for creating controls that are used in ARMO Platform and Kubescape.
From time to time, Kubernetes users and security experts need and want to write their own custom policies and controls to meet their specific needs and security policies. To do so, they need to know how to use OPA and Rego which isn’t trivial.
This is where AI comes in. ARMO Labs has harnessed GPT-3 to help users create their own custom controls without the need to know how to use OPA and Rego.
All they need to do is to write what they want to check in natural language. ARMO with GPT-3 will generate the exact control written in Rego, with the description and suggested remediation. Once the custom control is generated they can download it and run the control in the CLI, as part of improving your Kubernetes security posture.
This innovative feature from the ARMO Lab will be enhanced and improved over time as more and more users adopt it.
Access the functionality by signing in to ARMO Platform and navigating to Settings:
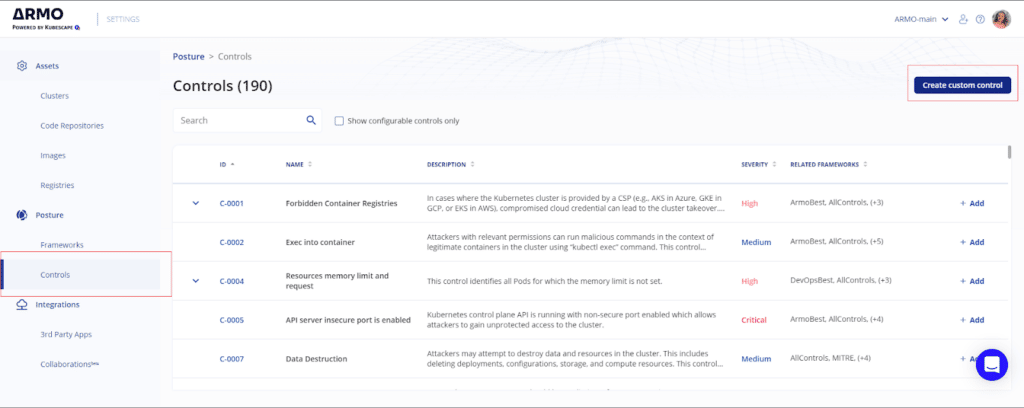
Select the Controls option from the menu and click on the Create custom control button.
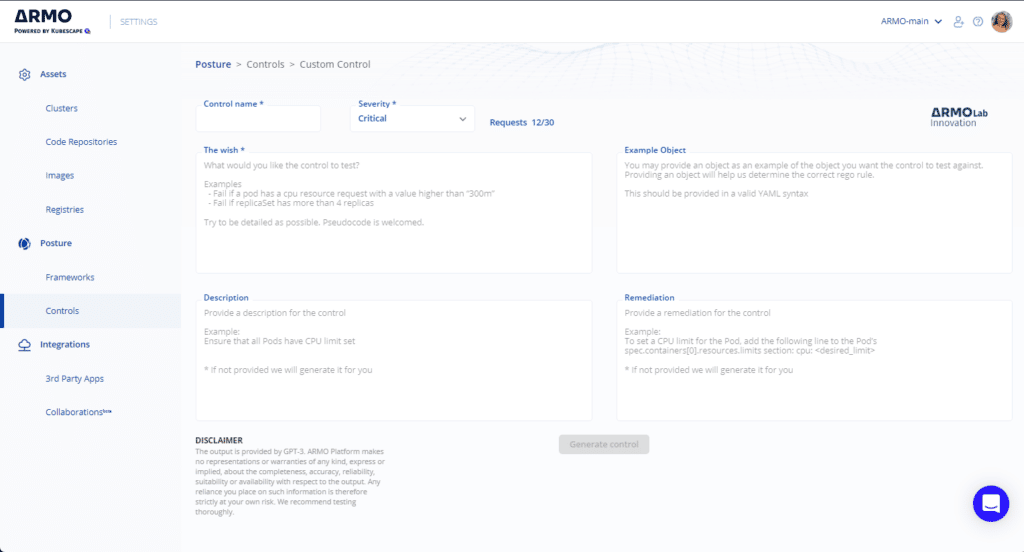
Enter your need in English in The Wish section, all the rest is optional!
If the optional fields are left empty, ARMO Platform will fill them in.
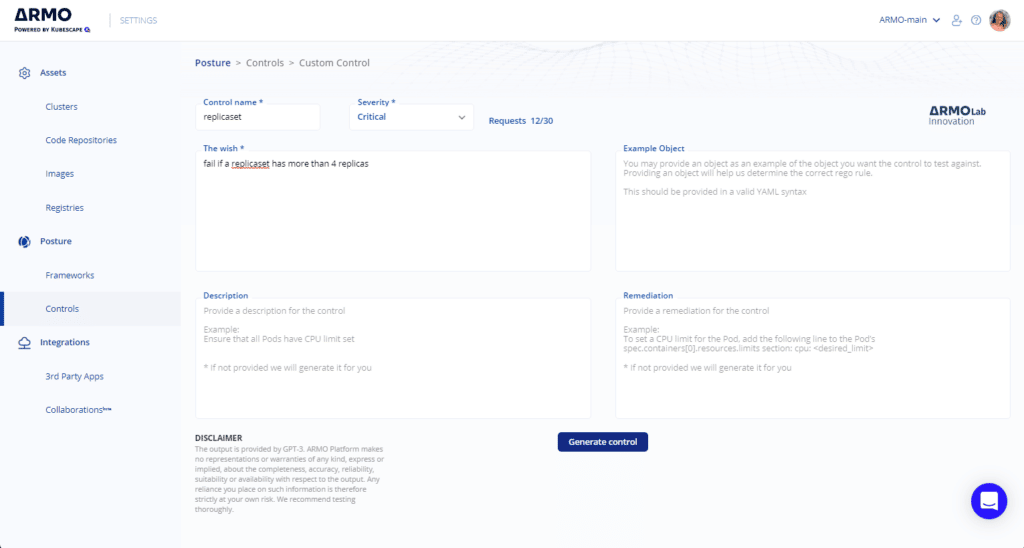
Click on Generate Control. During this step, ARMO Platform sends the information to GPT-3.
The result, including the rule, the description and the suggested remediation are generated and presented in the GUI.
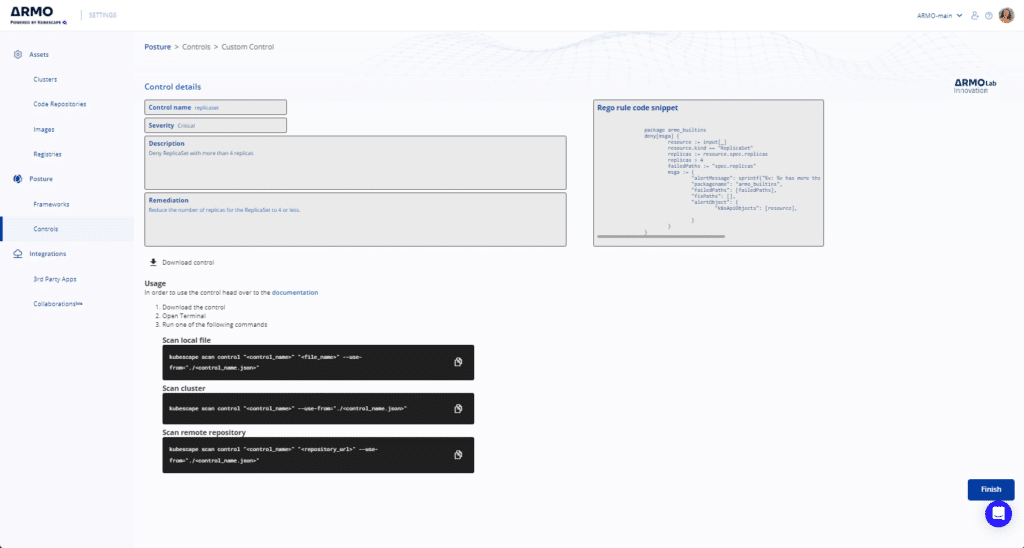
Please note, the result is generated by GPT-3 and is not verified to work. We encourage you to test the rule extensively, before adding it to your production environment.
Download the rule locally and run the custom control from the CLI.
There are many potential use cases for using ChatGPT within the context of Kubernetes.
Kubernetes can be challenging to navigate and fully utilize due to its complex nature and the need for a substantial understanding and set of skills. Any help that AI based tools, like ChatGPT, can provide to make these tasks easier, faster and automated will be successful. From writing a new YAML file, to deploying a new cluster, to securing it.
In the case of the implementation you just read about, we envision a custom framework, made up of custom controls, which will grow as you add controls to it. Our roadmap includes adding the ability to create custom frameworks that will host and save all custom controls and enable the users to run them directly from ARMO Platform. Thus, making it easier for users to access and utilize their custom controls, as well as streamline the process of adding new ones. This new type of custom framework, will provide a more flexible and user-friendly experience for our users.
In terms of upstream Kubescape. Users will be able to contribute new controls to the Kubescape Rego library and give back to the community in that way. Once merged, this control will be available for selection and use to all users of Kubescape and ARMO Platform.
Sign up for ARMO Platform today and join the future of Kubernetes security, today.

The only runtime-driven, open-source first, cloud security platform:
Continuously minimizes cloud attack surface
Secures your registries, clusters and images
Protects your on-prem and cloud workloads

Introduction: Luring in the Threat Actors The best way to understand real-world attacks is to...

Software supply chain attacks cost businesses $45.8 billion globally in 2023 alone, and is projected...
As organizations increasingly adopt cloud-native architectures, they face a sprawling attack surface with novel threats...